My CTF team, Kern(a)l, placed in the top 50 at HuntressCTF 2025. Shoutout to:
Follow The Money
Hey Support Team,
We had a bit of an issue yesterday that I need you to look into ASAP. There’s been a possible case of money fraud involving our client, Harbor Line Bank. They handle a lot of transfers for real estate down payments, but the most recent one doesn’t appear to have gone through correctly.
Here’s the deal, we need to figure out what happened and where the money might have gone. The titling company is looping in their incident response firm to investigate from their end. I need you to quietly review things on our end and see what you can find. Keep it discreet and be passive.
I let Evelyn over at Harbor Line know that someone from our team might reach out. Her main email is offline right now just in case it was compromised, she’s using a temporary address until things get sorted out:
[email protected]IMPORTANT: This challenge uses a non-standard flag format.
This challenge has two flags: the hacker’s username and the flag.
Looking at the ZIP file, we can see that there are 5 .eml files inside.
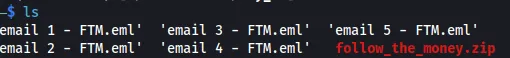
Since there was a breach in the company, and we obtained email files, the first thing that should come to mind is phishing. Phishing is a social engineering technique that threat actors use to manipulate someone into doing something their not supposed to. One of the most common ways of phishing is to send a noticeable email that looks professional and appears to be from someone who looks legit. In this email, they will supply their own malicious URL, and if the user clicks it and supplies data, they could get compromised. Sometimes, threat actors try to make the domain as closely related to the target as possible. This is known as typosquatting. This can be as simple as a mistyped domain, but it looks very similar to the target.
Using an Email Analyzer (shoutout to chubbychicken for the resource), we can begin reviewing each email file to identify which URLs it contains. Most of the emails have evergatetitle.netlify.app as a URL.
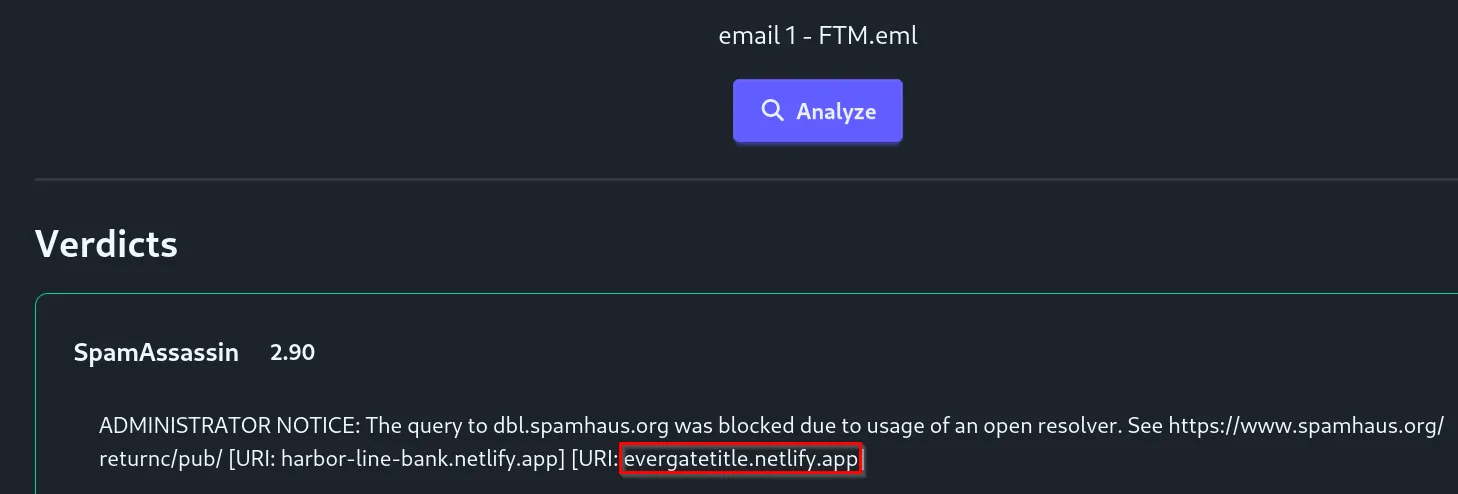
However, in email 5 - FTM.eml, we see that there is a typo in the URL, replacing the i with I: evergatetItle.netlify.app
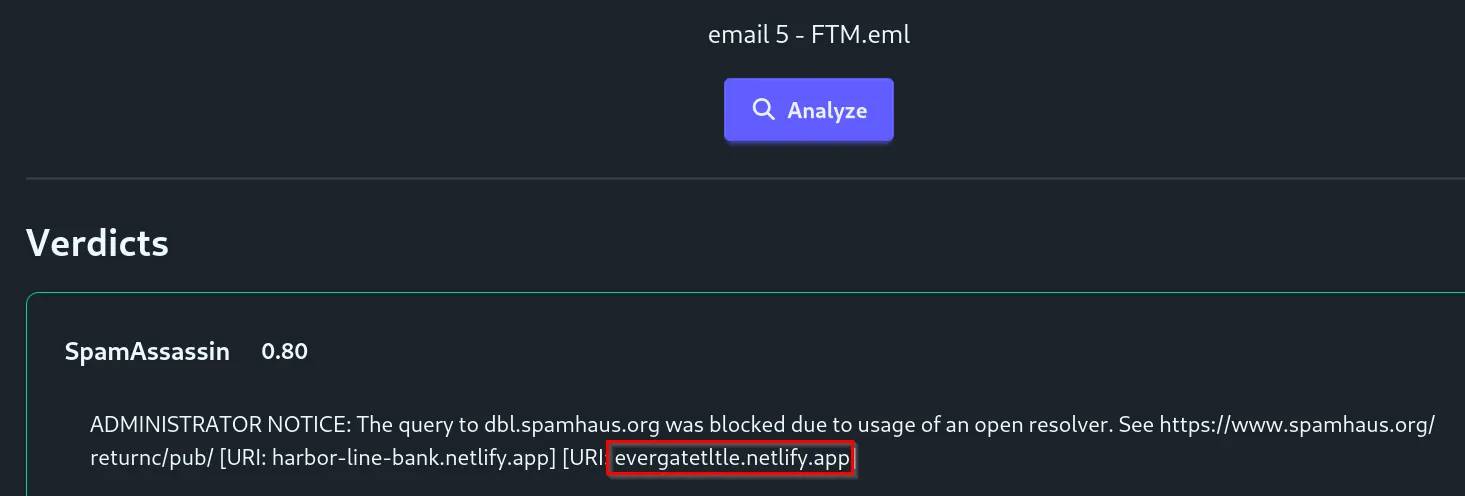
See how easy it is to overlook this small typo? With this URL, we can see what the “malicious” website is.
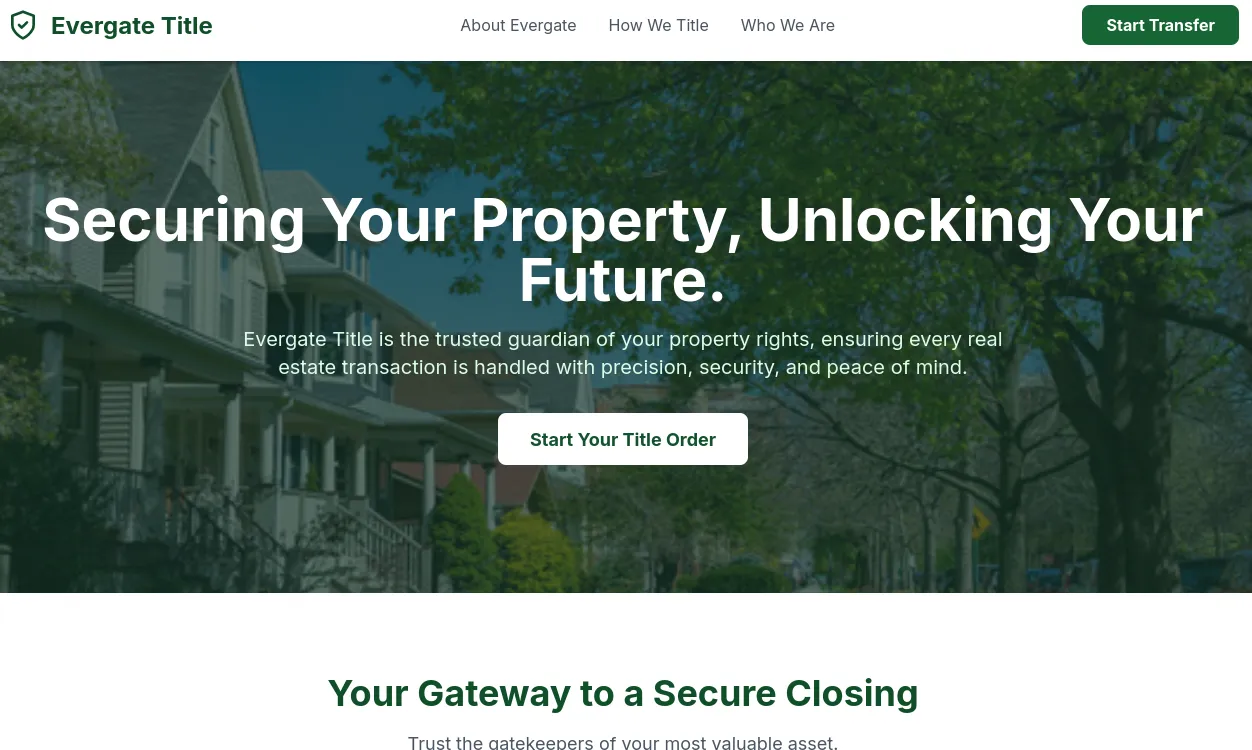
Scrolling down the webpage, we see there’s a Transfer Closing Funds button. Clicking on that, we see the webpage has a matrix-style background and a form for the user to fill out.
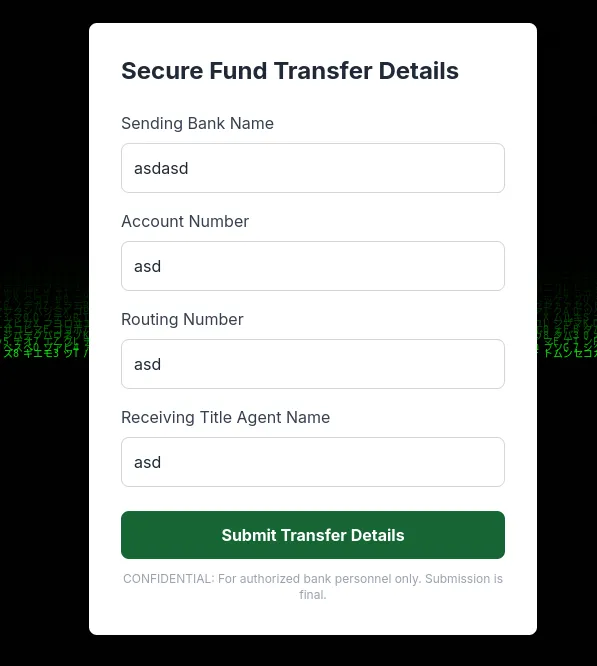
After submitting the data, we see a modal appear on the webpage that has a base64 string.
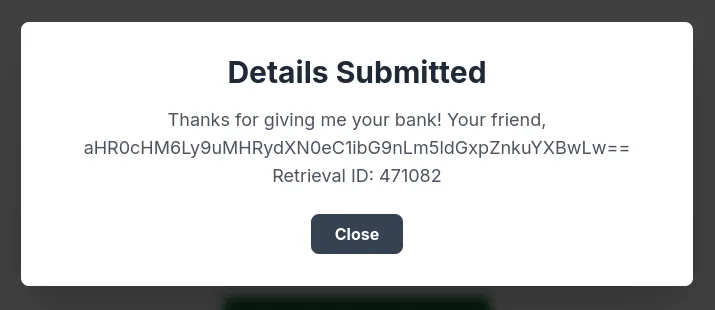
Thanks for giving me your bank! Your friend, aHR0cHM6Ly9uMHRydXN0eC1ibG9nLm5ldGxpZnkuYXBwLw==
Retrieval ID: 471082
Decoding the base64, we retrieve another URL to access.
echo "aHR0cHM6Ly9uMHRydXN0eC1ibG9nLm5ldGxpZnkuYXBwLw==" | base64 -d
https://n0trustx-blog.netlify.app/
What is the username of the hacker?: n0trustx
Navigating to the website, there is a Github button at the bottom.
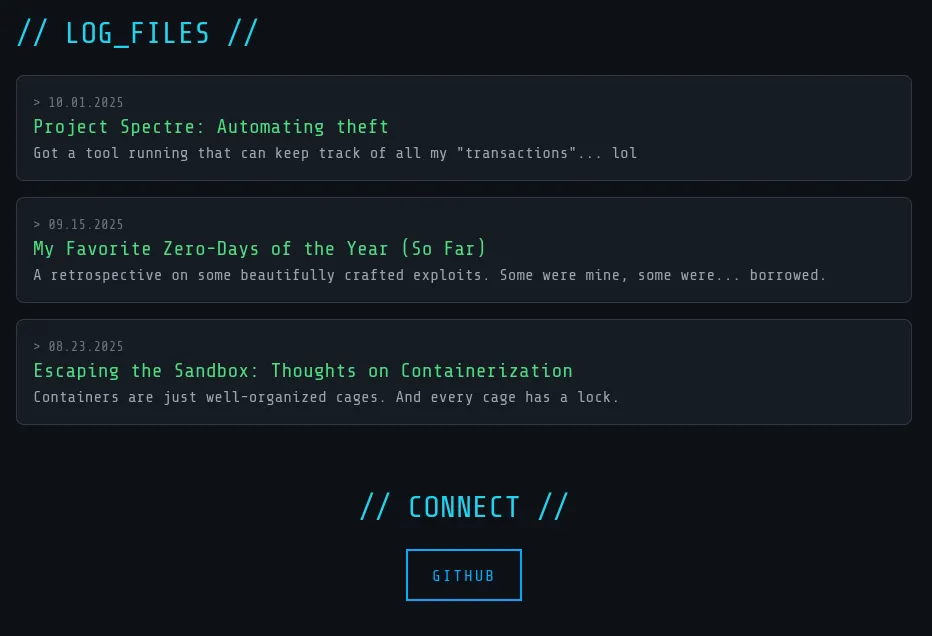
Clicking on it, we access n0trustx Github repository.
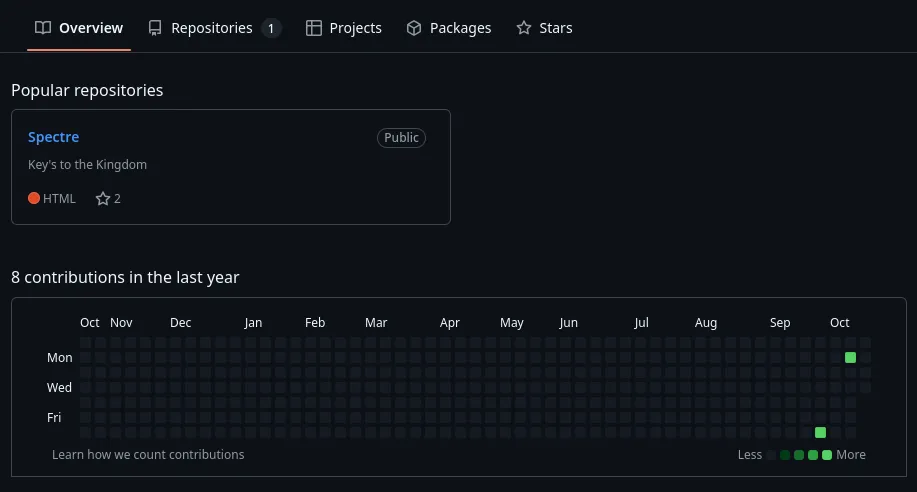
There is one repository on GitHub named Spectre. Looking at the repository’s contents, we see an HTML file.
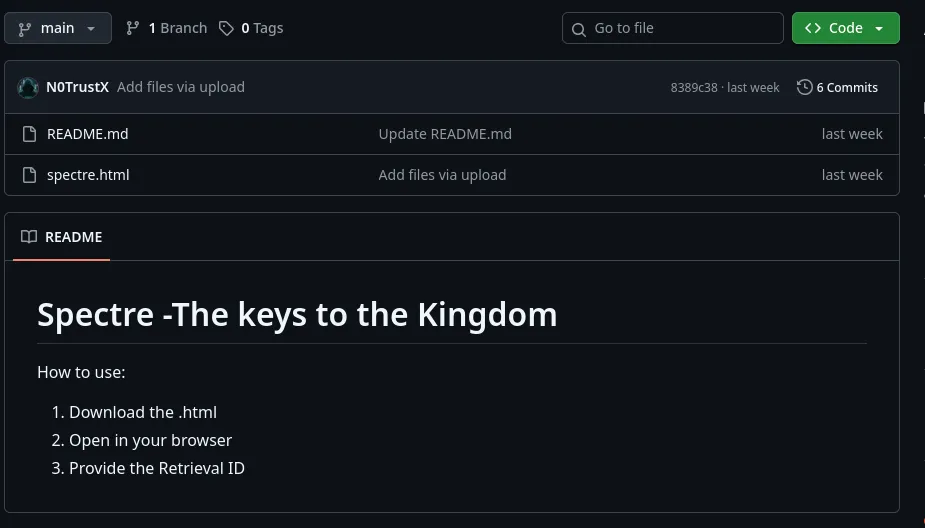
In the HTML file, there is a hidden div tag that has base64 inside with the name encodedpayload.
<!-- The Base64 encoded object is stored here, hidden from view -->
<div id="encodedPayload" class="hidden">ZmxhZ3trbDF6a2xqaTJkeWNxZWRqNmVmNnltbHJzZjE4MGQwZn0=</div>
Decoding the base64, we can retrieve the flag.
echo "ZmxhZ3trbDF6a2xqaTJkeWNxZWRqNmVmNnltbHJzZjE4MGQwZn0=" | base64 -d
Flag: flag{kl1zklji2dycqedj6ef6ymlrsf180d0f}
Follow The Money - The Sequel
The initial Follow the Money challenge should be completed first before this challenge.
Hey Support Team,
Thanks for your help the other day! After seeing the way you handled yourself and gathered these details, I wanted to see if I could get a bit more help from you. I know you found their username the other day. See what you can do with that. I need you to find the town that this hacker lives in. I don’t think the IR firm is doing enough. I want to have every piece of information we can find. Maybe we can pay a visit. Let me know what you find. Thanks!
This challenge DOES NOT require you to contact any businesses. This can be fully solved with publicly available information. Being that this is OSINT and public-facing, please DO NOT do anything to disrupt other CTF players or others that are not involved with the CTF.
What town does our hacker friend live in?
Since we already know the user’s name is n0trustx, we can begin searching through social media platforms and find him.
In Instant Username, we see that a few social media platforms have this username set to unknown.
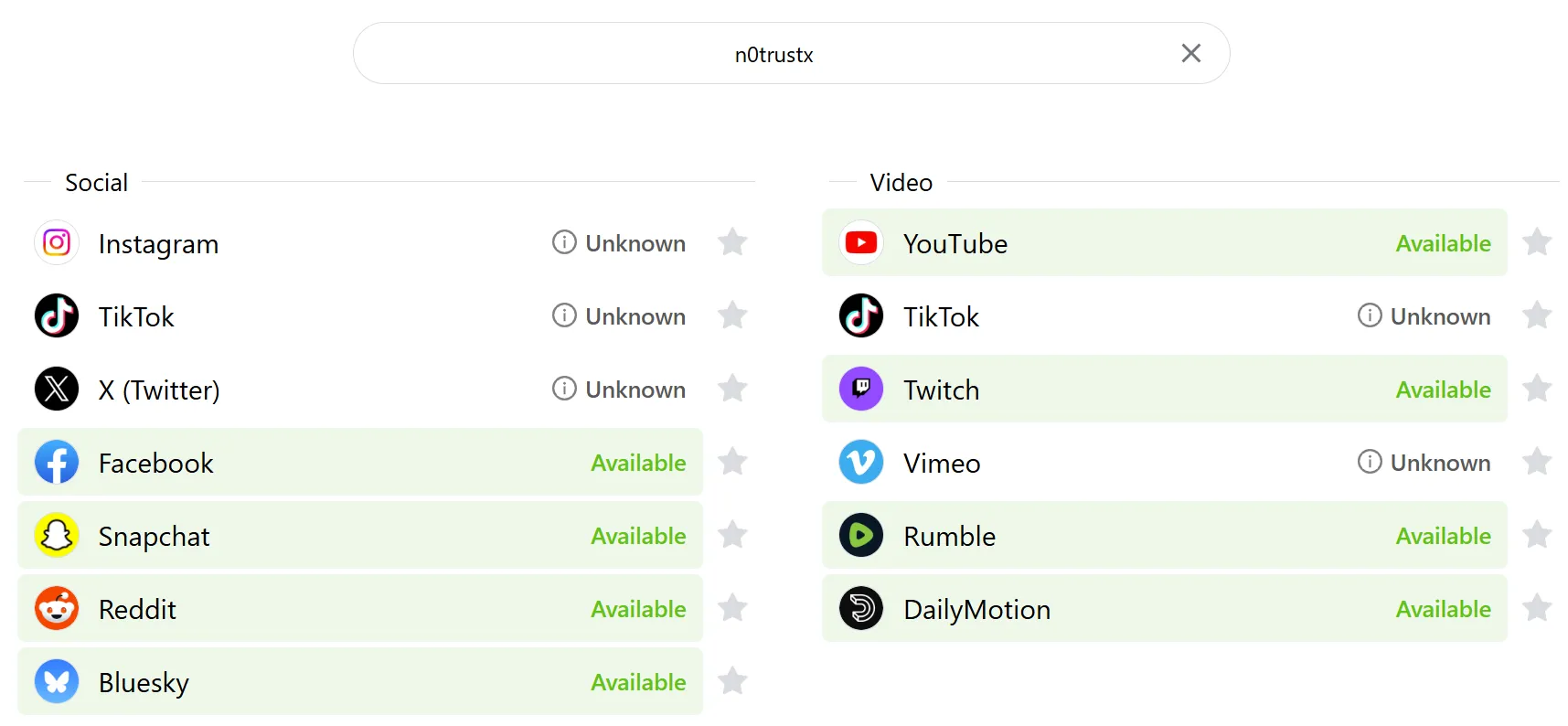
Looking through each social media platform, we see that the X account has the same profile as the GitHub we saw in the previous Follow The Money challenge. In the description, there are some octal characters, and the hacker seems to be posting consistently on the platform. We can decode the octal messaging using CyberChef.
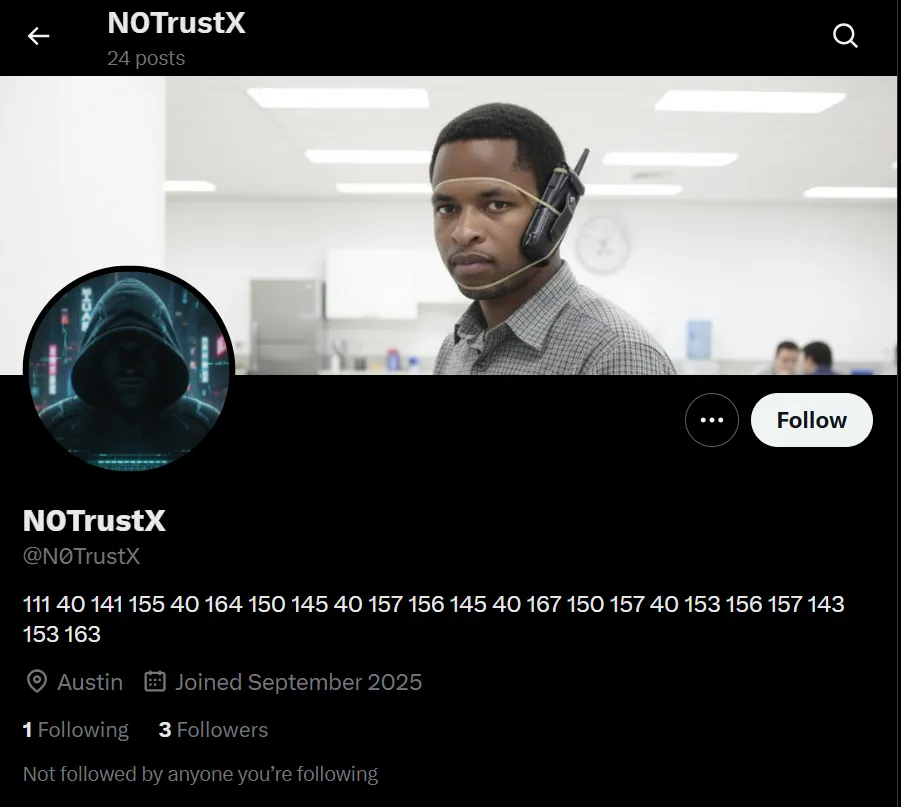
111 40 141 155 40 164 150 145 40 157 156 145 40 167 150 157 40 153 156 157 143 153 163
I am the one who knocks
However, we need to find the town where the hacker resides. On one of the posts, n0trustx a reply to a previous post made about how quiet the place he is located is, and that no one will know.
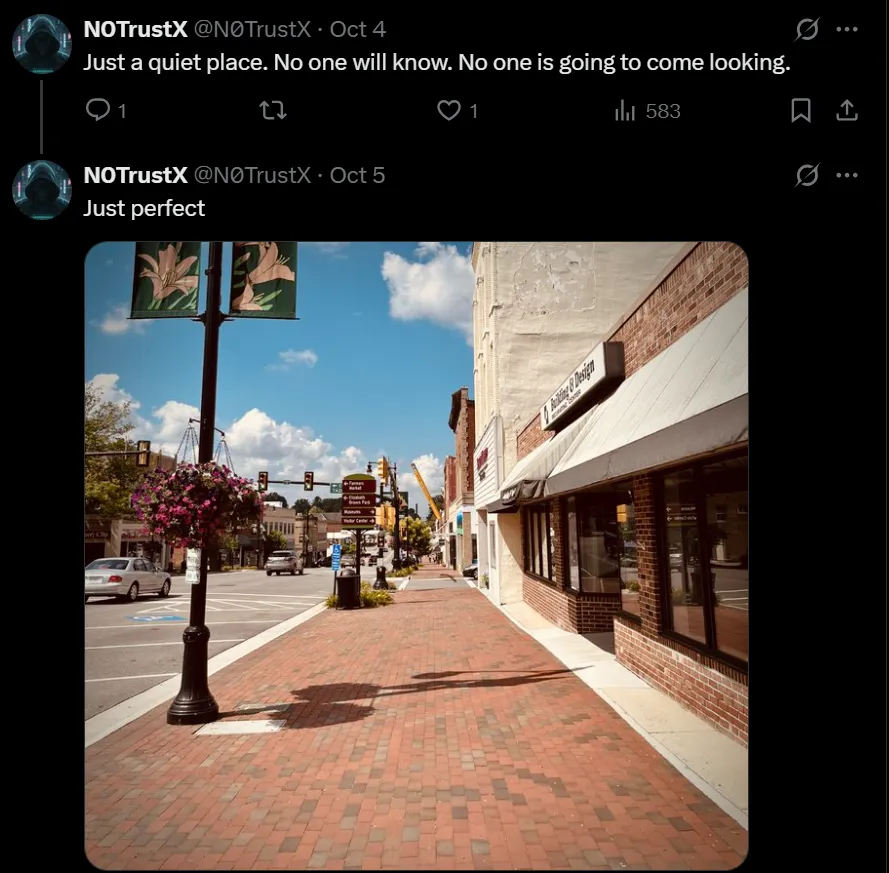
By taking the image and searching for it on Google, we can identify the location.

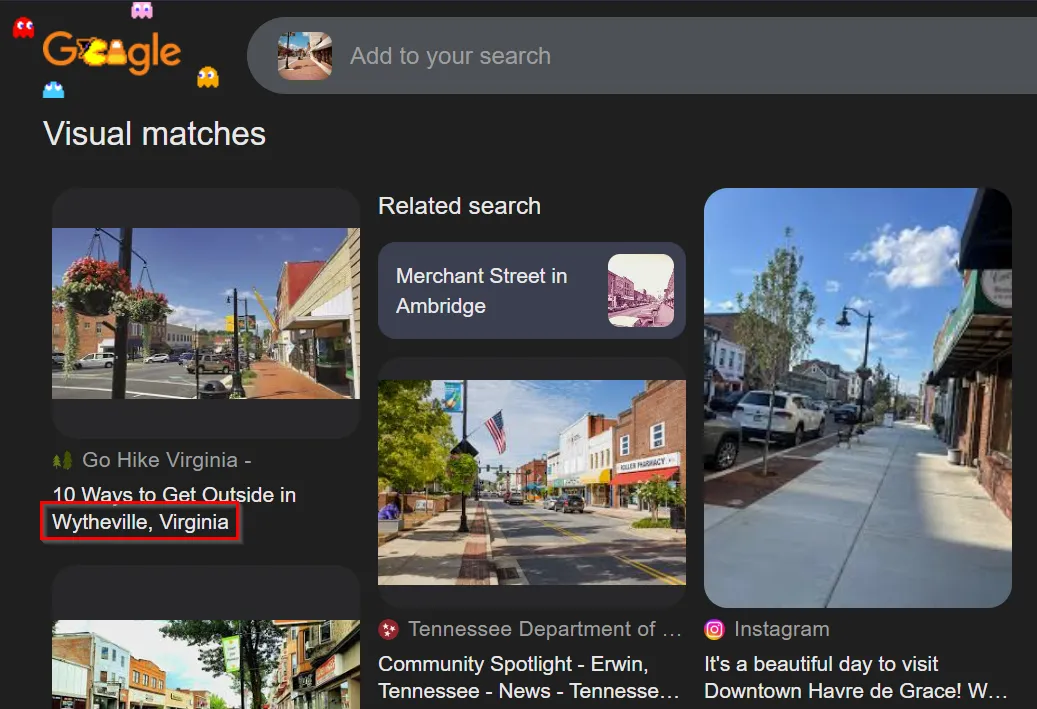
Flag: Wytheville
Can you find the nearby flag?
Now that we have the town, we need to identify the nearby flag. Looking at the original image, we can see there is a shop called Building & Design Decoration Center. Looking this up, we retrieve the address of the company.
130 East Main St., Wytheville, Va 24382
In the X postings, n0trustx keeps referring to Java and has a coffee emoji.
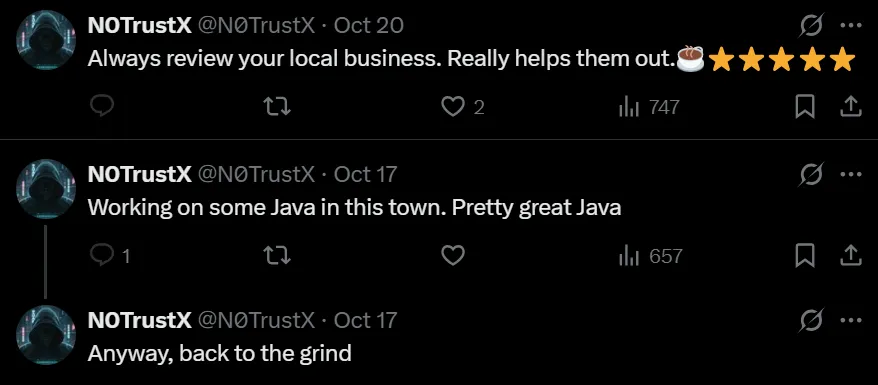
This is a clear indicator that we need to look at local coffee shops in the area. In the October 20th post, we also see 5-star emojis, which suggest we may be seeking a review of the coffee shop. Looking up Coffee shops on East Main St, Wytheville, VA 24382. The first coffee shop that comes up is The Grind.
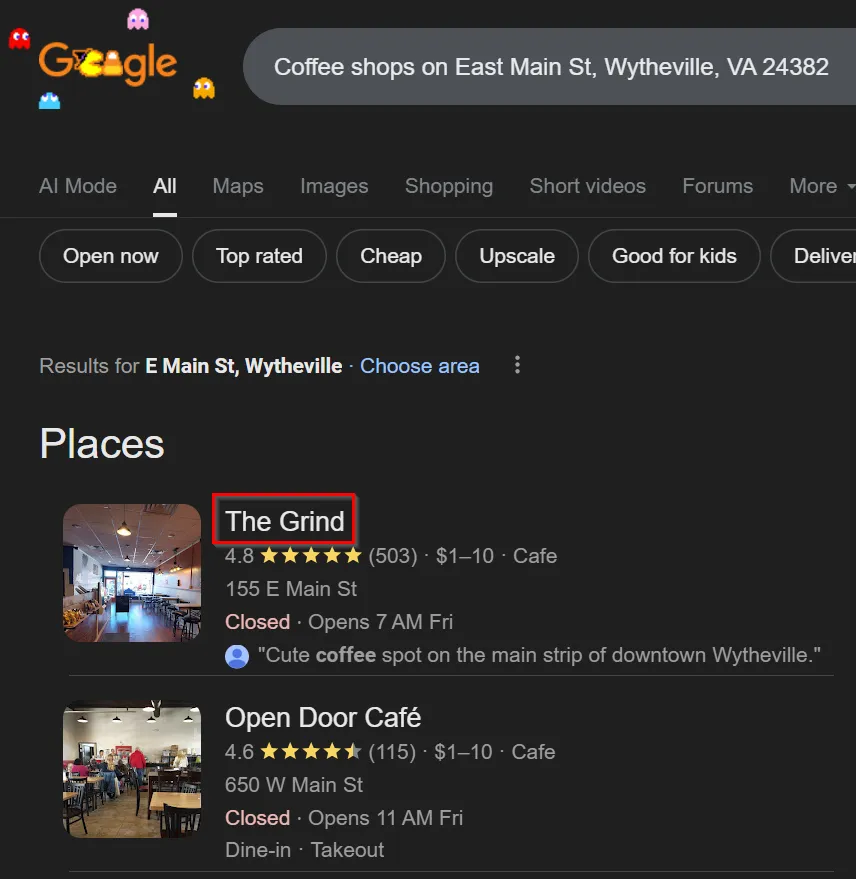
Looking at the Newest In reviews, we can see that one user has left a 5-star review and, at the bottom, shows the flag.
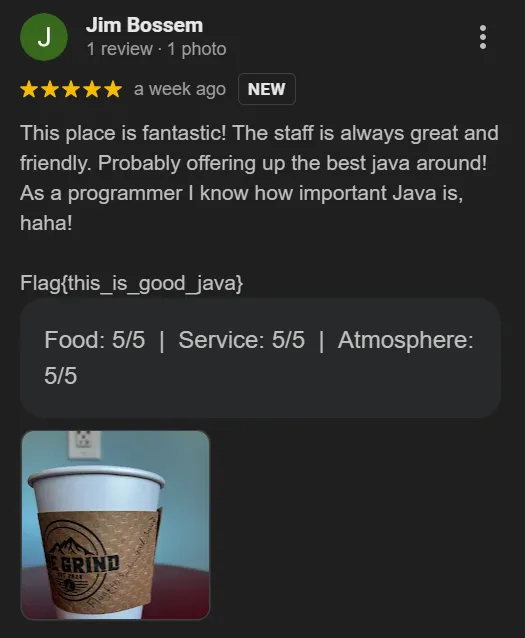
Flag: flag{this_is_good_java}
Authors

Lead Technical Writer
Evan is a dedicated cybersecurity professional with a degree from Roger Williams University. He is certified in GRTP, OSCP, eWPTX, eCPPT, and eJPT. He specializes in web application and API security. In his free time, he identifies vulnerabilities in FOSS applications and mentors aspiring cybersecurity professionals.
Recent Posts

React2Shell Unauthenticated RCE (CVE-2025-55182) – Full Exploit Walkthrough | P3rf3ctR00t 2025 CTF
Comprehensive PerfectRoot 2025 CTF writeup: detailed walkthroughs of authentication bypass, React2Shell RCE, and SSTI!
Dec 9, 2025

HuntressCTF 2025 Malware Challenges – Writeups & Analysis
Learning about malware analysis through HuntressCTF challenges. Deobfuscate code and using Telegram API to retrieve the flag.
Nov 1, 2025

HuntressCTF 2025 Miscellaneous Challenges - Full Writeups
Explore the unexpected in HuntressCTF 2025 Misc challenges. Creative puzzles, crypto quirks, and logic traps that test your problem-solving edge.
Nov 1, 2025

