My CTF team, Kern(a)l, placed in the top 50 at HuntressCTF 2025. Shoutout to:
Read The Rules
Please follow the rules for the Huntress CTF!
Read the rules at https://ctf.huntress.com/rules
If you look closely, you can find a flag!
Looking at the rules page, we see it’s standard and not much is going on.
Going to Page Source, we see something a little suspicious.
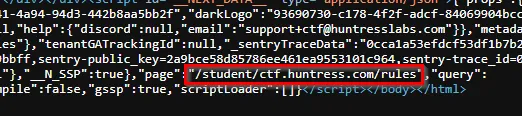
Currently, we are at the /rules endpoint, but navigating to the /student/ctf.huntress.com/rules endpoint didn’t reveal anything interesting. Actually, it’s the exact same page! Since this is a NextJS application, we can view some of the JS files in the Sources section of Inspect. In the file structure, we can see the exact path that is shown in the Page Source.
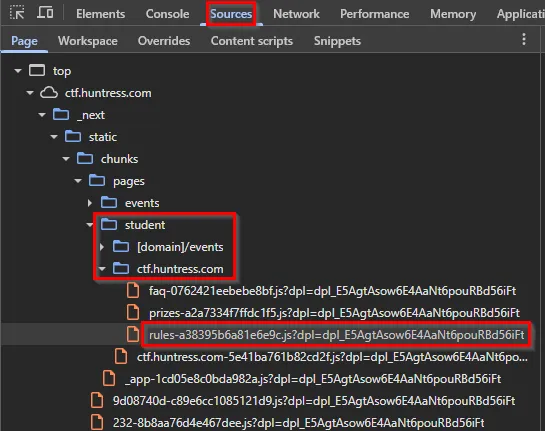
Click on the rules.js In the file, we see a commented-out flag.
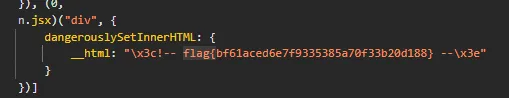
Flag: flag{bf61aced6e7f9335385a70f33b20d188}
Technical Support
Want to join the party of GIFs, memes and emoji shenanigans? Or just want to ask a question for technical support regarding any challenges in the CTF? Be sure to join the Huntress CTF Discord server.
This CTF uses support tickets within Discord to help handle requests.
If you need assistance, please create a ticket with the
#ctf-open-ticketchannel. You do not need to direct message any CTF organizers or facilitators, they will just tell you to open a ticket. You might find a flag in the ticket channel, though!
Looking at the Discord channel #ctf-open-ticket, in the description of the channel, there is a flag.
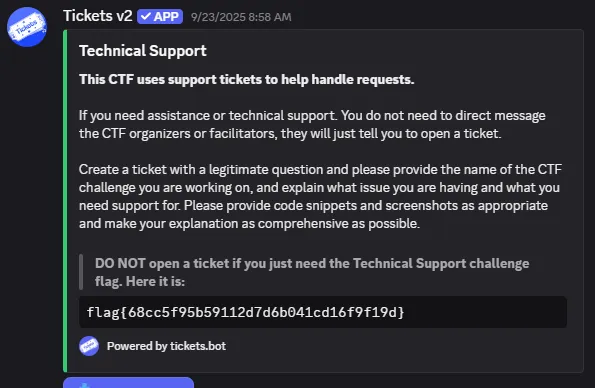
Flag: flag{68cc5f95b59112d7d6b041cd16f9f19d}
Spam Test
Time to do some careful Googling… what’s the MD5 hash of the Generic Test for Unsolicited Bulk Email (GTUBE) string?
Submit the hash wrapped within the
flag{prefix and}suffix to match the standard flag format.
Looking up the string on Google, we see there is a Wikipedia that has the MD5 sum for us.
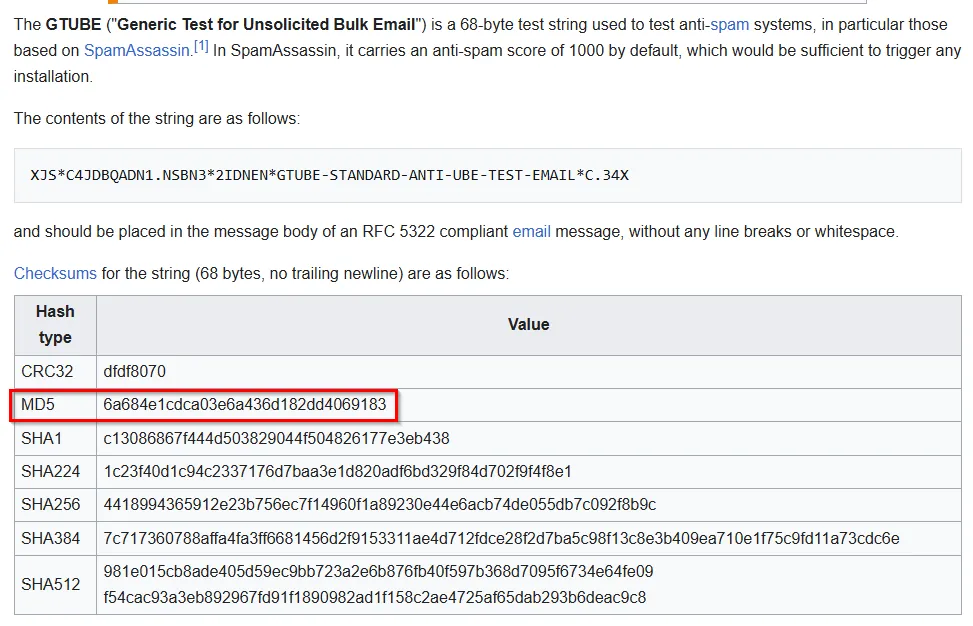
Flag: flag{6a684e1cdca03e6a436d182dd4069183}
Cover All Your Bases
Can you make sense of all the different data below? Each one has a different representation!
Uncover the appropriate plaintext and submit the flags below! Do you know what all these ones and zeros mean?
01000111 01110010 01100101 01100001 01110100 00100000 01110111 01101111 01110010 01101011 00100001
00100000 01010100 01101000 01100001 01110100 00100000 01110111 01100001 01110011 00100000 01000010
01100001 01110011 01100101 00100000 00110010 00101100 00100000 01100010 01100101 01110100 01110100
01100101 01110010 00100000 01101011 01101110 01101111 01110111 01101110 00100000 01100001 01110011
00100000 01100010 01101001 01101110 01100001 01110010 01111001 00101110 00100000 01001001 01110100
00100000 01101111 01101110 01101100 01111001 00100000 01110101 01110011 01100101 01110011 00100000
01110100 01110111 01101111 00100000 01110011 01111001 01101101 01100010 01101111 01101100 01110011
00111010 00100000 00110000 00100000 01100001 01101110 01100100 00100000 00110001 00101100 00100000
01110111 01101000 01101001 01100011 01101000 00100000 01101101 01100001 01101011 01100101 01110011
00100000 01101001 01110100 00100000 01100101 01100001 01110011 01111001 00100000 01110100 01101111
00100000 01110011 01110000 01101111 01110100 00101110 00100000 01000001 01101110 01111001 01110111
01100001 01111001 00101100 00100000 01101000 01100101 01110010 01100101 00100111 01110011 00100000
01111001 01101111 01110101 01110010 00100000 01100110 01101100 01100001 01100111 00111010 00100000
01100110 01101100 01100001 01100111 01111011 00110110 00110111 00111000 01100001 01100011 00110100
00110101 00110100 00111000 00110111 01100011 00111001 00111000 00110110 00110010 01100001 00110110
01100011 00110010 01100011 00110000 00110000 01100001 00110001 01100001 01100110 01100110 01100101
01100100 00111001 01100100 01100011 01111101
This is binary, which can be converted using a website such as CyberChef.
Great work! That was Base 2, better known as binary. It only uses two symbols: 0 and 1, which makes it easy to spot. Anyway, here's your flag: flag{678ac45487c9862a6c2c00a1affed9dc}
Flag: flag{678ac45487c9862a6c2c00a1affed9dc}
Hmmm, a group of triplets, it looks like. Can you find out what they are trying to say?
116 151 143 145 154 171 040 144 157 156 145 041 040 124 150 141 164 040 167 141 163 040 102 141 163
145 040 070 054 040 157 162 040 157 143 164 141 154 056 040 111 164 040 165 163 145 163 040 144 151
147 151 164 163 040 060 055 067 054 040 141 156 144 040 157 146 164 145 156 040 163 150 157 167 163
040 165 160 040 151 156 040 146 151 154 145 040 160 145 162 155 151 163 163 151 157 156 163 040 157
156 040 114 151 156 165 170 056 040 123 160 157 164 040 151 164 040 167 150 145 156 040 156 165 155
142 145 162 163 040 150 141 166 145 040 154 145 141 144 151 156 147 040 060 163 056 040 110 145 162
145 047 163 040 171 157 165 162 040 146 154 141 147 072 040 146 154 141 147 173 146 145 065 070 060
145 060 065 145 065 062 067 146 062 060 064 062 061 062 071 060 066 060 065 070 060 071 143 141 145
143 071 175
This is Base8 (or Octal), and we can use CyberChef to decode it and retrieve the flag.
Nicely done! That was Base 8, or octal. It uses digits 0-7, and often shows up in file permissions on Linux. Spot it when numbers have leading 0s. Here's your flag: flag{fe580e05e527f20421290605809caec9}
Flag: flag{fe580e05e527f20421290605809caec9}
These numbers look familiar… but how could they be represented as text?
089 111 117 032 099 114 097 099 107 101 100 032 105 116 033 032 084 104 097 116 032 119 097 115 032
066 097 115 101 032 049 048 044 032 111 117 114 032 101 118 101 114 121 100 097 121 032 100 101 099
105 109 097 108 032 115 121 115 116 101 109 046 032 073 116 032 114 117 110 115 032 102 114 111 109
032 048 045 057 032 097 110 100 032 108 111 111 107 115 032 108 105 107 101 032 110 111 114 109 097
108 032 110 117 109 098 101 114 115 046 032 069 097 115 121 032 116 111 032 105 100 101 110 116 105
102 121 033 032 089 111 117 114 032 102 108 097 103 058 032 102 108 097 103 123 055 100 049 101 098
050 101 048 055 055 054 099 100 055 099 053 099 055 056 100 102 048 049 048 049 048 102 051 048 101
053 048 125
This is Decimal, and we can use CyberChef to retrieve the flag.
You cracked it! That was Base 10, our everyday decimal system. It runs from 0-9 and looks like normal numbers. Easy to identify! Your flag: flag{7d1eb2e0776cd7c5c78df01010f30e50}
Flag: flag{7d1eb2e0776cd7c5c78df01010f30e50}
These look like pairs! But these have weird letters in them?
41 77 65 73 6f 6d 65 20 6a 6f 62 21 20 54 68 61 74 20 77 61 73 20 42 61 73 65 20 31 36 2c 20 6f 72
20 68 65 78 61 64 65 63 69 6d 61 6c 2e 20 49 74 20 75 73 65 73 20 30 2d 39 20 61 6e 64 20 41 2d 46
2c 20 6f 66 74 65 6e 20 77 69 74 68 20 70 72 65 66 69 78 65 73 20 6c 69 6b 65 20 30 78 2e 20 43 6f
6d 6d 6f 6e 20 69 6e 20 6d 65 6d 6f 72 79 20 64 75 6d 70 73 20 61 6e 64 20 63 6f 6c 6f 72 20 63 6f
64 65 73 2e 20 48 65 72 65 20 69 73 20 79 6f 75 72 20 66 6c 61 67 3a 20 66 6c 61 67 7b 64 33 63 62
32 62 65 33 65 34 65 34 61 38 66 35 31 37 64 39 63 35 63 65 34 33 37 32 62 30 62 37 7d
Again, we can use CyberChef since this is hexadecimal.
Awesome job! That was Base 16, or hexadecimal. It uses 0-9 and A-F, often with prefixes like 0x. Common in memory dumps and color codes. Here is your flag: flag{d3cb2be3e4e4a8f517d9c5ce4372b0b7}
Flag: flag{d3cb2be3e4e4a8f517d9c5ce4372b0b7}
Uppercase letters and digits in a long stream… notice anything about the padding?
I5XW6ZBAO5XXE2ZBEBKGQYLUEB3WC4ZAIJQXGZJAGMZCYIDPMZ2GK3RAOVZWKZBA
NFXCAR3PN5TWYZJAIF2XI2DFNZ2GSY3BORXXEIDLMV4XGLRAJF2CA5LTMVZSAQJN
LIQGC3TEEAZC2NZOEBEWMIDZN52SA43FMUQGY33UOMQG6ZRAOVYHAZLSMNQXGZJA
NRSXI5DFOJZSAYLOMQQGI2LHNF2HGLBAORUGS3TLEBBGC43FGMZC4ICHMV2CA5DI
MF2CAZTMMFTSCIDGNRQWO6ZZMJRDKYTCHBSWCNJQHBRGGZTCMM2TCYTEGVSTCMLF
MZRDEOLDMN6Q====
This is Base32, which CyberChef can perform and retrieve the flag.
Good work! That was Base 32, often used in Google Authenticator keys. It uses A-Z and 2-7. If you see lots of uppercase letters and digits, think Base32. Get that flag! flag{9bb5bb8ea508bcfbc51bd5e11efb29cc}
Flag: flag{9bb5bb8ea508bcfbc51bd5e11efb29cc}
A mixed alphabet with symbols. What is this one supposed to be?
K19X CSUEWQE24EBWE3/DK848UAIECV44HECN34HECDZC0R61Q57%E CH44M-DSCAB44V3E6$CE4404
EQ34CYA8T8D3D3WE5UD-M8*+APR8IN85LEREDOEDIEC6$CI$5*C9T44LQE.OEOCCJ$DH8FX3EK447$C7
WE4LE1Q5AVCD3DLWE1Q5CECRTC-QEC$D*3EBPEU34SUE*VD%3E.OEKFE*EDIQDA448%EC44Z CV3E6$C
B44TVDCEC4WDI$5Y69O/E944E44PVDV1DE44PVDV3DVICYJCI-C4:6846:/6A46YICJOCGM64ECYJCKA
7YJC2R6J-CZ2
This is Base45, and once again, can be decoded using CyberChef.
Great spotting! That was Base 45, used in QR codes for EU Digital COVID Certificates. It uses a mix of letters, digits, and symbols. It looks quirky but decodes cleanly. Have a flag! flag{b5bef376027104b8c73dafbe95be47f4}
Flag: flag{b5bef376027104b8c73dafbe95be47f4}
Compact and common on the wire… does the ending give you a clue?
V2VsbCBkb25lISBUaGF0IHdhcyBCYXNlIDY0LCBzdXBlciBjb21tb24gZm9yIGVuY29kaW5nIGRh
dGEgaW4gZW1haWwgYW5kIHdlYiB0cmFmZmljLiBMb29rIGZvciBBLVosIGEteiwgMC05LCBwbHVz
ICsgYW5kIC8sIGFuZCBzb21ldGltZXMgdGhlIHBhZGRpbmcgPSBzaWducyBhdCB0aGUgZW5kLiBG
bGFnOiBmbGFne2NkMDE2NGZmNjQ3MjZmMjk3MmIyZDhmMmFjMDExOWRifQ==
Finally, we have some Base64 action! This can be decoded using CyberChef as well.
Well done! That was Base 64, super common for encoding data in email and web traffic. Look for A-Z, a-z, 0-9, plus + and /, and sometimes the padding = signs at the end. Flag: flag{cd0164ff64726f2972b2d8f2ac0119db}
Flag: flag{cd0164ff64726f2972b2d8f2ac0119db}
This variant often shows special markers. See anything bracketing the data?
<~:2+3L+EqaECEXg"BOQ!*G@>P86=FqH+?250+EqL5@qZupDf'',+DG^9A8,XfATD@"F<Ga8EbSs"FE9
&W<+ohc6"FnCAM6>j@qfX:2'@'NEbSs"F<G^IF^]*&Gp%0M@<-I2+EqOABHTEd+CT.u+D#G$F!,[@FD)
eG4t[sWBOr;a7RJ:Q3ANE6G%#E*@;^00F`V,8+CQC%Ec5AsATAo%CiF&r@V'X(.!]`R+DkP4+EM+*+Cf
(nEa`I"ATDi7Ch[Zr+FYja?n<FI/0JkO+FP[k+A$/fH#IhG+Co%nDe*F"+Cf>,E,8rsDK?q/@W-C2+DG
_:@;KXg+EMgF@W-((/0K"XBlmiu+EV:.+@9LXAN2OiG%#E*@;^0>+@^0UB0%/ICggt'@5K\q@:_,Q2D[
<IA2uM-1h/C&AN)S+@P_LS2.U<.I/~>
This is Base85 and can be decoded using CyberChef.
Nice work! That was Base 85, which comes in different variants. The Adobe/Ascii85 variant usually starts with <~ and ends with ~>. The RFC 1924 variant uses a broader alphabet (you may see characters like ~, `, {, or }). If your decoder complains about invalid symbols, switch the Base85 variant. Flag: flag{a414ae096381d9594c58e785b3c95dfb}
Flag: flag{a414ae096381d9594c58e785b3c95dfb}
This noisy alphabet is picky about whitespace… formatting might matter!
@D_<sB5GVmj-;A[GD:PIptd9#KgRoG![3\gx4mcIUAiYA8M=E_=UOU5S$HqE$p<KHnvkV66}Q?tqB]P)Dy\4O\cT$^qE;BG\LX&pVXaZ$Tq0,'1:I3jzOY4Rs}8iY(1.GjE2RDb#yuj-*n10I1S\d:W-#pm0',!eD:H4sK'c@^jAiC%1K}1^V65i/Upa*U(mEU'(Va'b/nt_*vgYH.^_V_Td5AgNoIWlD9jvOZ3oKhm/WwX+-GHriuce$TlHB+#)E]kGisTc:ehwoA<RF;gx-ld->om0iC&$I3SXV_'bF.gOk[#-H,1kv93JUpCu&I-r4c^^pu+!?9iXkKdk6,1cPeWN.@E?CO
This is Base92, and we can decode it using CyberChef.
Very nice! That was Base 92. Many decoders do not ignore whitespace, so you may need to remove line breaks before decoding. Tip: Base92 uses a wide printable set but excludes spaces and newlines; strip them before decoding. Here is another flag: flag{0c97042d855d7b353dc87c91ea902129}
Flag: flag{0c97042d855d7b353dc87c91ea902129}
The data below looks super weird! Don’t panic if your editor can’t render every symbol. Can you tell what it is?
𖡅驣ꍬ𐙥啴𒁪噢褠陨啴陷啳陂驳欠樵欳唬鵷顩啨陣啮陭啰𒁴𐘠陥ꍲ啹𔑥𓁥啹𐙕顩饯啥鵣𓁡顡驴捲縠啦𒁹啵驳啥鹷饬ꔠ𖡩𓅥𒀠啦饯啤ꍧ𒅹𓅨阠饮𓄠ꕹ𒁢𓅬唬𒁹啵𓁡啥𓁰靯靡𖥬ꌠ𒁯鹫鱮阠啴鵴𓅩售驈驲鸠啳𒁹𓁵鬠𐙩ꍡ鬠陬潧鬠陬𠅧樴昷椷餵饣餴欱浦此敦污饦魡昷朵頸ᕽ
This was an interesting one! Most people know about Base64, Base32, Base85, etc etc. Did you know there is something called Base65536? By going to this website, we can decode the message and retrieve the flag.
Excellent job! That was Base 65536, which can map to nearly every Unicode character. If you see wild mixes of odd glyphs and symbols, you are probably looking at this. Here is your final flag: flag{4571745dcd4d16f8d6f0a7fdaf71528c}
Flag: flag{4571745dcd4d16f8d6f0a7fdaf71528c}
Just a Little Bit
If just a little bit were to go missing… would it really even matter?
11001101101100110000111001111111011011001011000110110011011001111000110110001011011001110011100001110010111000101100100110011001100101100101110010101100110110001110010101100110111000011100101101011100100011010101110010110110011011011001000111001011001111001101111101
Entering the above information into Dcode.fr shows that it detects several options, with the highest likelihood being ASCII Code.
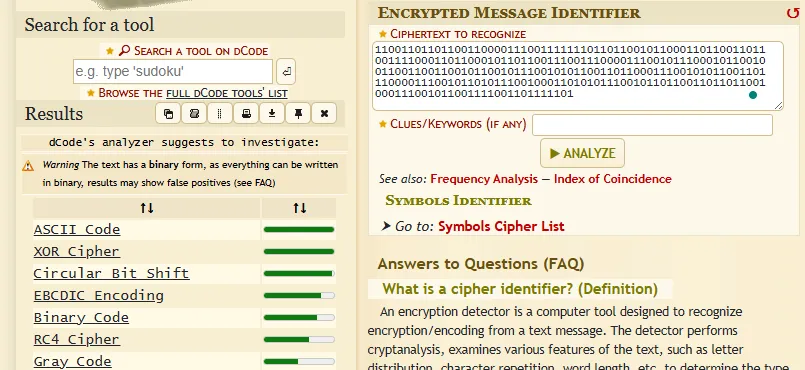
Navigating to the ASCII Code section of the application, we can supply the data and retrieve the flag.
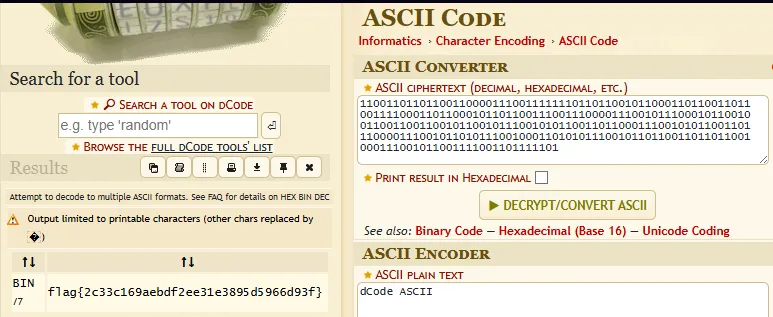
Flag: flag{2c33c169aebdf2ee31e3895d5966d93f}
QRception
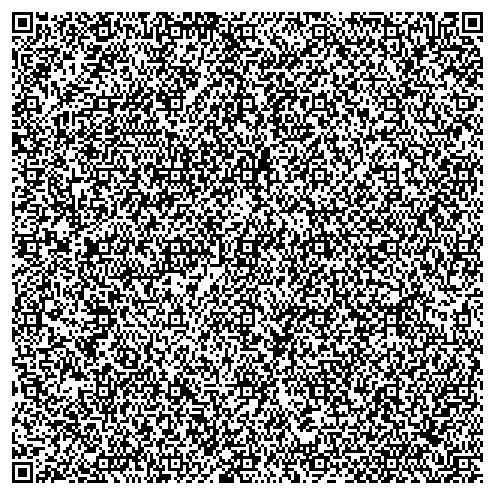
Wow, that’s a big QR code! I wonder what it says!
This is a giant QR code. The first thing that I like to try is using QR codes and sending them through a QR code converter to see if it can extract text. Using this website, we can upload the image and see what text comes back.
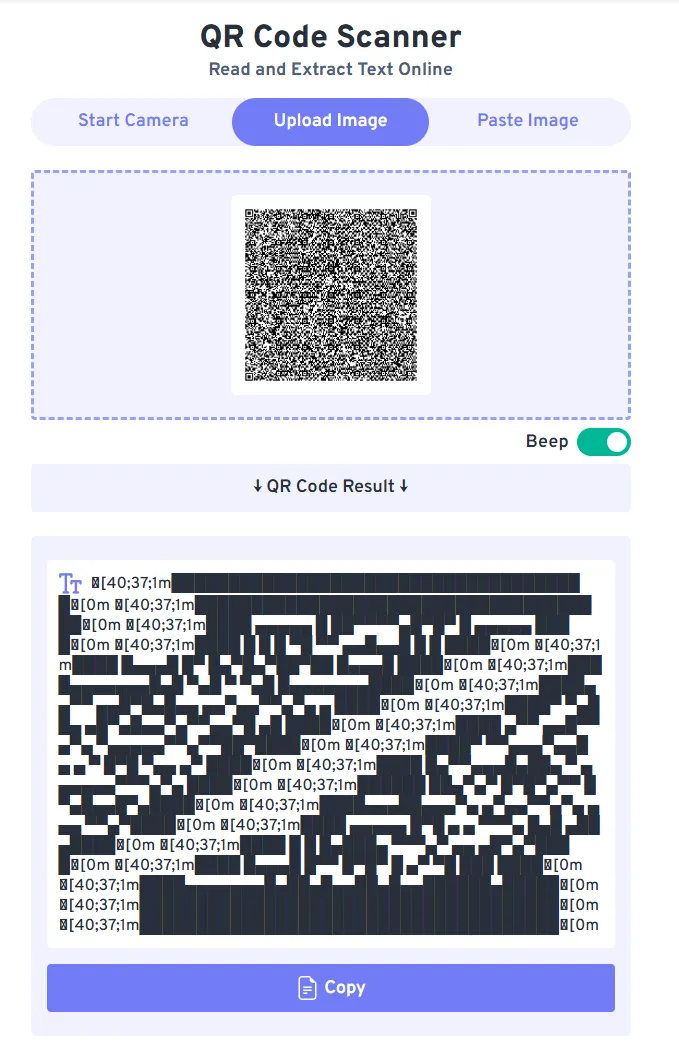
[40;37;1m█████████████████████████████████████[0m
[40;37;1m█████████████████████████████████████[0m
[40;37;1m████ ▄▄▄▄▄ █ ██▀▀▀▀▄█▀█▀ █ ▄▄▄▄▄ ████[0m
[40;37;1m████ █ █ █ ▀█ ▀▀ ▄▄█▄▄█ █ █ ████[0m
[40;37;1m████ █▄▄▄█ █▀ █▄▀█▄▀██▀██ █▄▄▄█ ████[0m
[40;37;1m████▄▄▄▄▄▄▄█▄█ ▀▄█ ▀ ▀▄█ █▄▄▄▄▄▄▄████[0m
[40;37;1m████▄▄▀▀ ▄▄█▀█▄█▄▄ ▄▄▀▄▄▀▀▄▀▄ ▄ ████[0m
[40;37;1m████▀ ▀▄██▄ ▄█▀▄█▄▄▀▄▀▀▄▄▀█ ▄█ ████[0m
[40;37;1m████ ▄▀▀ ▄▄█▀▀▄▀▄ ▀▄▄▄▄▄▀▀▄▀▀██▀████[0m
[40;37;1m████▀ ▀▀▄▄▄▀▄▄█ ▄ ▄ ▀ █▀█ ▀▄▄ ▄▀ ████[0m
[40;37;1m████ █▄▀▀▄▄▄█▄██▄ ▀ ▄▄▄▄▄▄▀▀▀▄▀▄ ████[0m
[40;37;1m██████ ██▄▀▄▀ █▀█▀▄▀▀ █ ▀▄█▄▄█▀▄████[0m
[40;37;1m████▄▄▄██▄▄▄▀▄ ▄▀▄▄▀▀▄▀▄ ▄▄▄ ▀▀▄▀████[0m
[40;37;1m████ ▄▄▄▄▄ █▀█ ▄ ▄ ▀▀▀▄ █▄█ ▄██▄████[0m
[40;37;1m████ █ █ █▄███▄ ▀▀▀▄▀ ▄▄ ▄█▀▄▀████[0m
[40;37;1m████ █▄▄▄█ █▀▀ █▀█▀ █ ▄▀ ▀█ ███ ████[0m
[40;37;1m████▄▄▄▄▄▄▄█▄██▄█▄▄██▄█▄▄██████▄█████[0m
[40;37;1m█████████████████████████████████████[0m
[40;37;1m█████████████████████████████████████[0m
Looks like it is another QR code. In VSCode, we can beautify the QR code, then screenshot it and upload it back to the website, which reveals the flag.
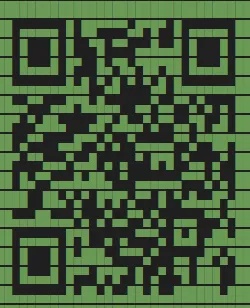
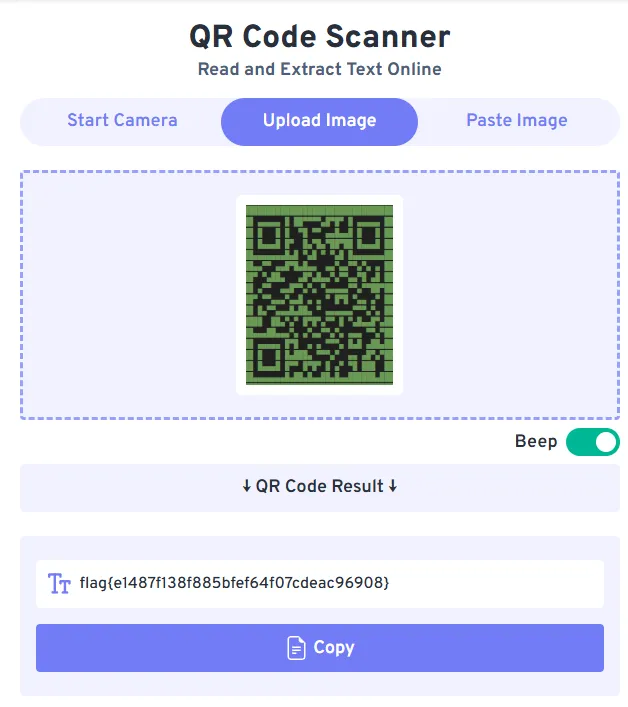
Flag: flag{e1487f138f885bfef64f07cdeac96908}
RFC 9309
Sorry. You know every CTF has to have it. 🤷
Looking at the application, we can see that it’s an RFC 9309 document about the Robots Exclusion Protocol (REP). This document refers to the robots.txt, which can be found on web applications to prevent crawlers, such as Google, from indexing the pages.
Going to the /robots.txt endpoint, we can see that it’s scrollable, which is most of the time not the case. Scrolling down, we see the flag.
User-Agent: *
Disallow: /
<...snip...>
flag{aec1142c199aa5d8ad0f3ae3fa82e13c}
Flag: flag{aec1142c199aa5d8ad0f3ae3fa82e13c}
OFA
Two factors? In this economy??!!
Looking at the web application, we see there is a login page.
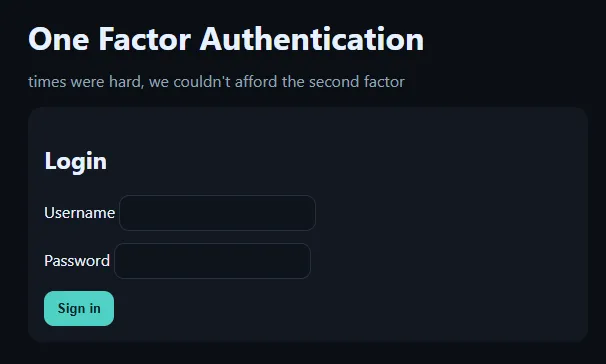
Since there are no credentials in the page source and no JavaScript for client-side authentication, we have to guess the username and password. The first thing I tend to try is admin:admin and admin:password for challenges like these.
Submitting the form, we see that admin:admin works.
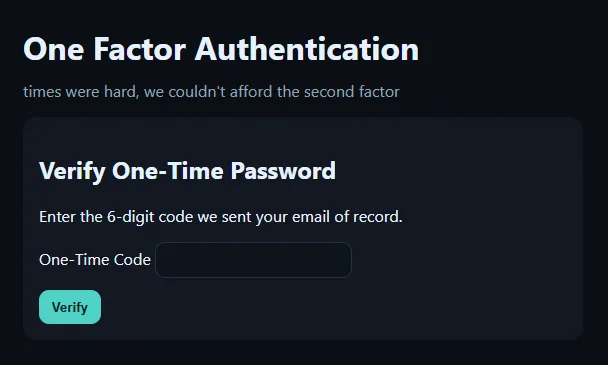
It looks like we need to find an OTP. Since we can’t bruteforce on this web application, we can check out the page source. Viewing it reveals the following JavaScript.
(function() {
const REAL = "103248";
const form = document.getElementById('otp-form');
const code = document.getElementById('code');
form.addEventListener('submit', function(e) {
const val = (code.value \ '').trim();
if (!/^\d{6}$/.test(val)) {
e.preventDefault();
alert('Please enter a valid 6 digit code.');
code.focus();
return;
}
if (val !== REAL) {
e.preventDefault();
alert('code does not match ' + REAL);
code.focus();
}
});
})();
We can see that the OTP is 103248. After supplying that to the form, we retrieve the flag.
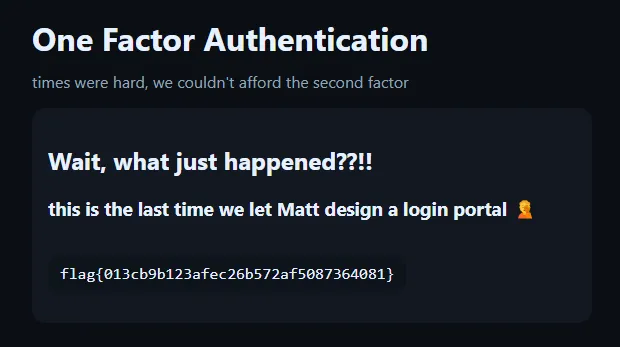
Flag: flag{013cb9b123afec26b572af5087364081}
Maximum Sound
Dang, this track really hits the target! It sure does get loud though, headphone users be warned!!
Doing a file command on the WAV file, we see that it is a WAV file
file maximum_sound.wav
maximum_sound.wav: RIFF (little-endian) data, WAVE audio, Microsoft PCM, 16 bit, mono 44100 Hz
Whenever there is something having to do with WAV files in a CTF, the first thing you should think of is Audio Steganography. One of the first steps in Audio Steganography is to add a Spectrogram layer to the audio to see the frequencies. To do this in Sonic Visualiser, select Layer -> Add Spectrogram (or Shift+G).
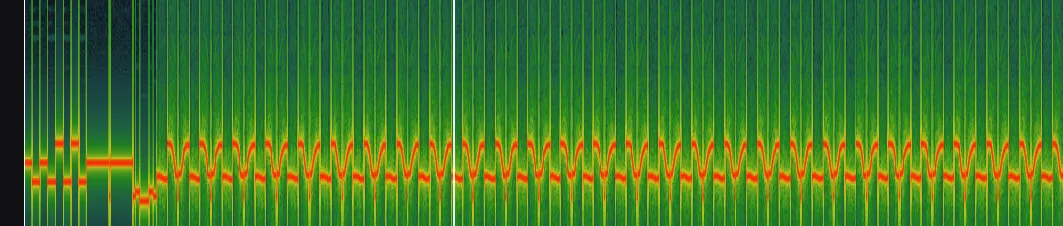
Originally, when I looked at this, I thought it might have something to do with Morse code, but after further research, that was a dead end. I kept looking for different techniques to use on audio files for steganography when I stumbled upon Sumit Arora’s blog post. In it, he mentions something about Slow-Scan Television (SSTV). The image on the blog looked similar to the one above, so I dug deeper.
SSTV is a method for sending radio transmissions that are converted into an image. Looking through Google, I found this website that decodes SSTV audio files. After submitting the WAV file and uploading it to the website, I received an image!

This image appears to be a barcode, but not a standard one, such as a QR code. I ran a reverse image search on the retrieved image and discovered it was a Maxicode Barcode.
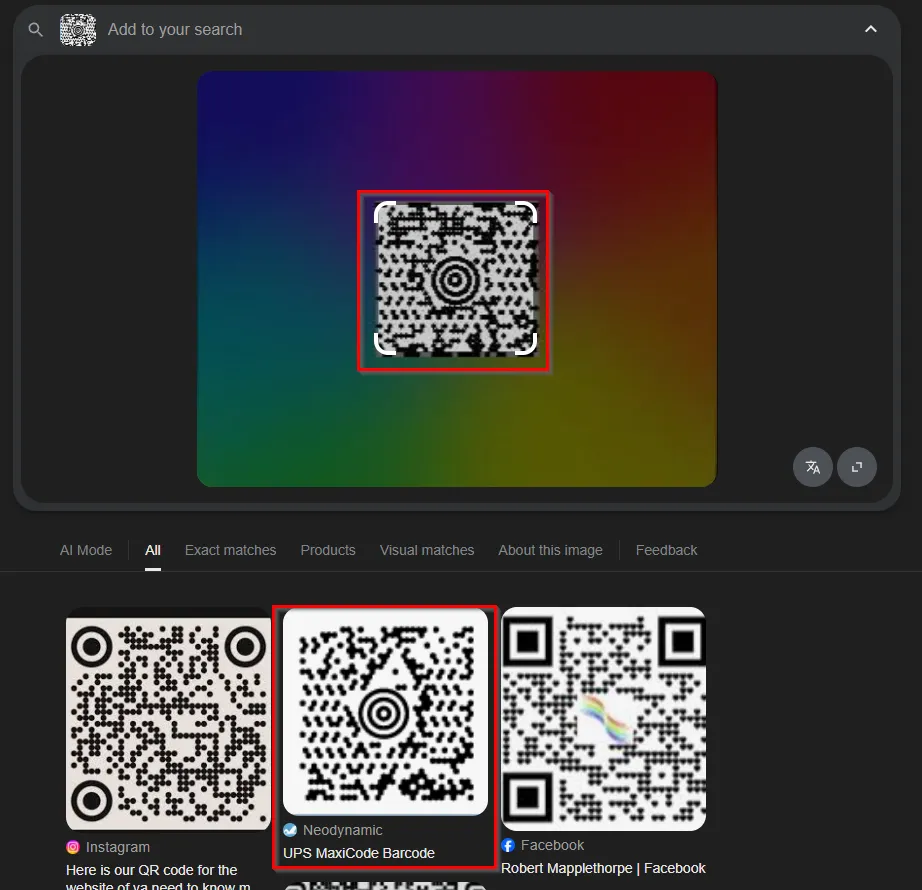
We are on the right track! Searching for Maxicode image readers online, I found this website that decodes the Maxicode Barcode and retrieves the flag.
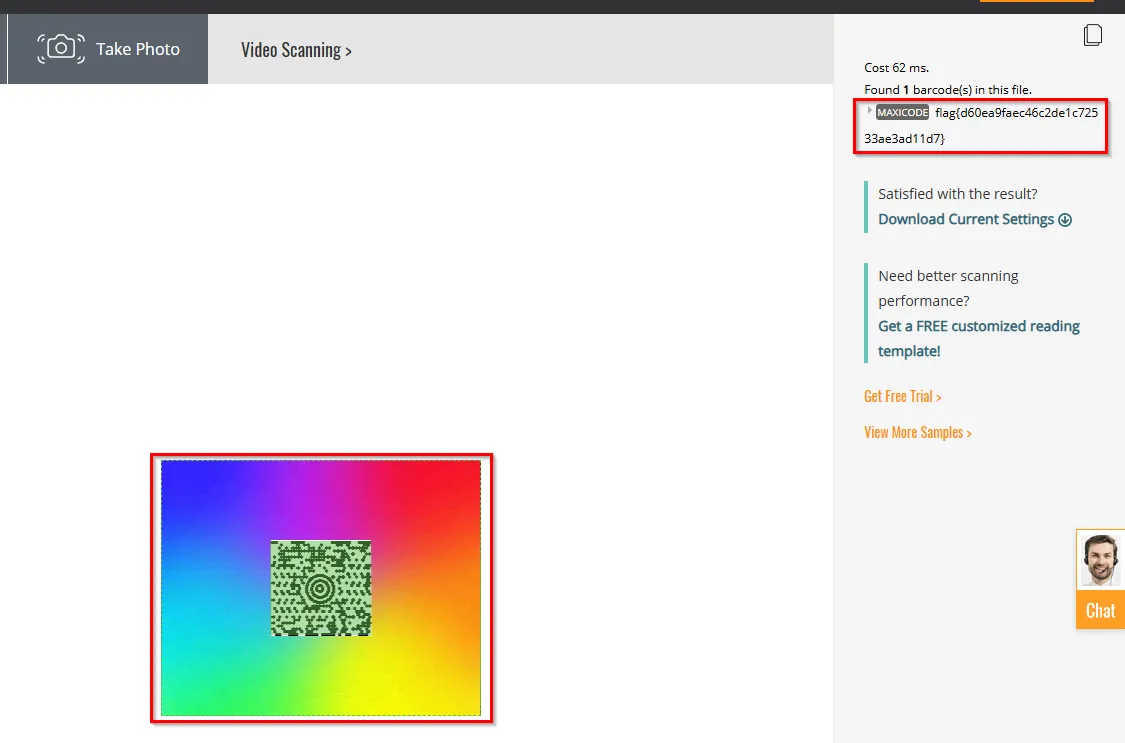
Flag: flag{d60ea9faec46c2de1c72533ae3ad11d7}
Snooze
Don’t bug me, I’m sleeping! Zzzz… zzz… zzzz…
After downloading the file, I ran a file command on it.
file snooze
snooze: compress'd data 16 bits
This is a compressed file, similar to gzip, zip, 7z, etc, except it was compressed using a tool called compress. In conjunction with this command, there is also an uncompress command that will uncompress the file. However, when you try to uncompress the file, you receive an error message.
uncompress snooze
gzip: snooze: unknown suffix -- ignored
Doing a quick Google search, I realized that the file needs to have a .Z extension.
mv snooze snooze.Z
From there, you can uncompress the file and read the flag.
uncompress snooze.Z && cat snooze
flag{c1c07c90efa59876a97c44c2b175903e}
Flag: flag{c1c07c90efa59876a97c44c2b175903e}
Authors

Lead Technical Writer
Evan is a dedicated cybersecurity professional with a degree from Roger Williams University. He is certified in GRTP, OSCP, eWPTX, eCPPT, and eJPT. He specializes in web application and API security. In his free time, he identifies vulnerabilities in FOSS applications and mentors aspiring cybersecurity professionals.
Recent Posts

React2Shell Unauthenticated RCE (CVE-2025-55182) – Full Exploit Walkthrough | P3rf3ctR00t 2025 CTF
Comprehensive PerfectRoot 2025 CTF writeup: detailed walkthroughs of authentication bypass, React2Shell RCE, and SSTI!
Dec 9, 2025

HuntressCTF 2025 Malware Challenges – Writeups & Analysis
Learning about malware analysis through HuntressCTF challenges. Deobfuscate code and using Telegram API to retrieve the flag.
Nov 1, 2025

HuntressCTF 2025 Miscellaneous Challenges - Full Writeups
Explore the unexpected in HuntressCTF 2025 Misc challenges. Creative puzzles, crypto quirks, and logic traps that test your problem-solving edge.
Nov 1, 2025